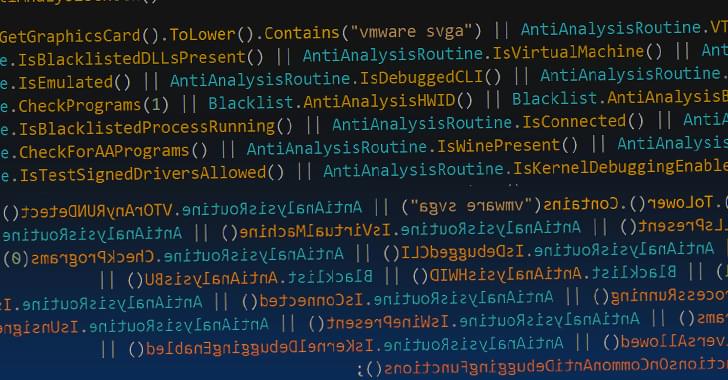
Besides incorporating more anti-analysis and anti-virtualization checks, Typhon Reborn V2 removes its persistence features, instead opting to terminate itself after exfiltrating the data.
The malware ultimately transmits the collected data in a compressed archive via HTTPS using the Telegram API, marking continued abuse of the messaging platform.
“Once the data has been successfully transmitted to the attacker, the archive is then deleted from the infected system,” Brumaghin said. “The malware then calls to terminate execution.”