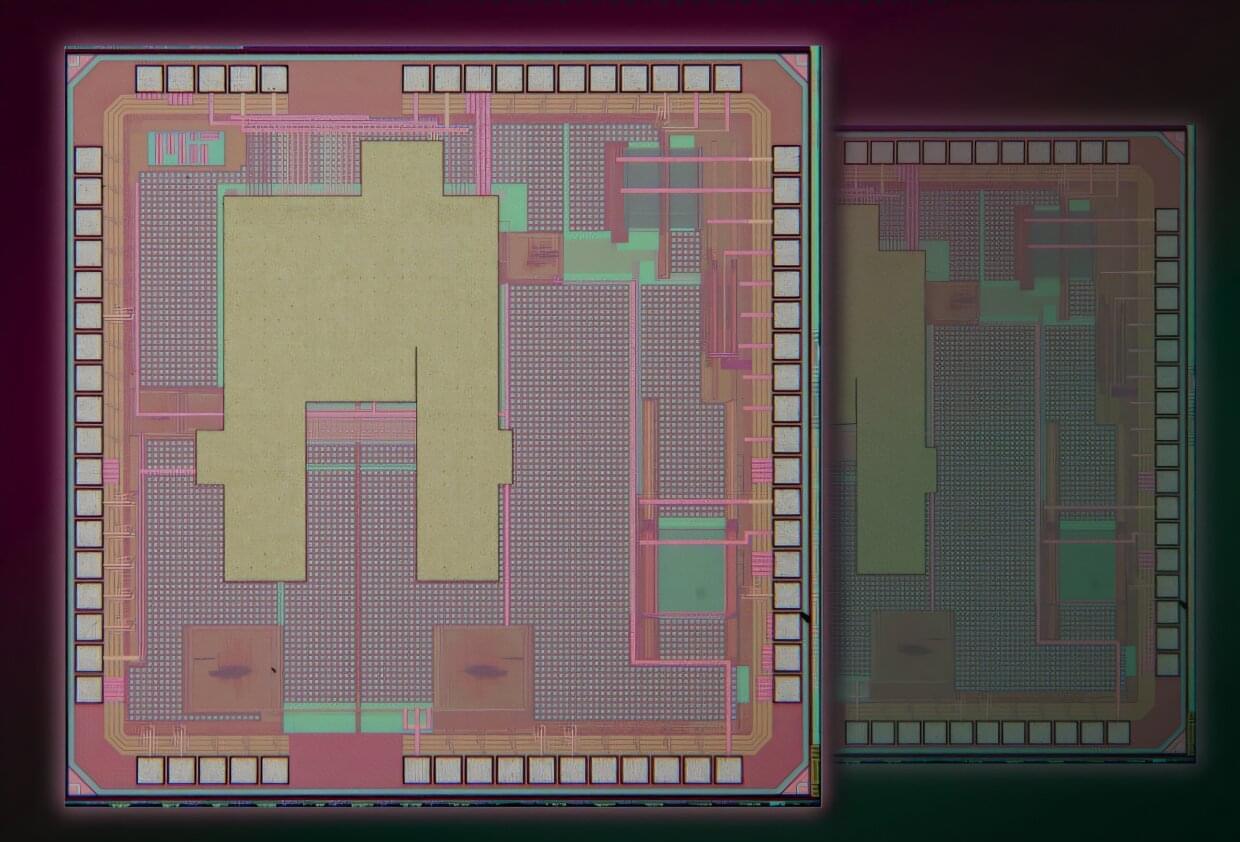
Sensors made of carbon nanotubes that can measure infrared and terahertz radiation are being tested for uses ranging from detecting damaged cables after earthquakes, to collecting health data via ultrathin wearable devices, and assisting with pharmaceutical quality control, say researchers in Japan.
“Accurately visualizing the internal structures of organisms and objects is integral to our daily lives, from medical imaging to security scanning in airports,” and terahertz sensors built from carbon nanotubes are uniquely suited to this purpose, says Yukio Kawano is a professor of engineering at Chuo University in Tokyo, and project leader at the Kanagawa Institute of Industrial Science and Technology (KISTEC) in Japan.
Compared with many sensor technologies that can only detect one part of the electromagnetic spectrum, Kawano’s team is working to create sensors that can detect terahertz and a broader range of radiation, and use them to produce high-resolution images.