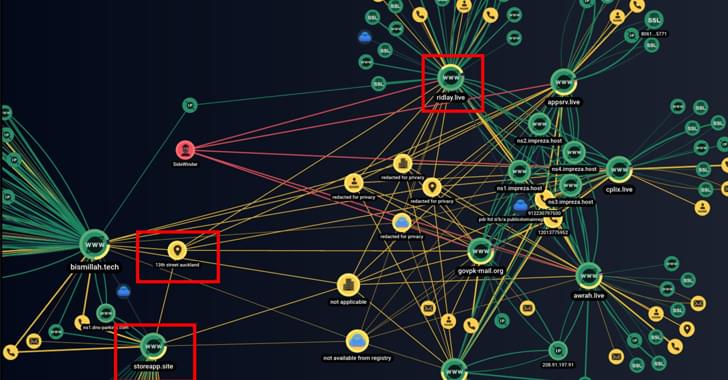
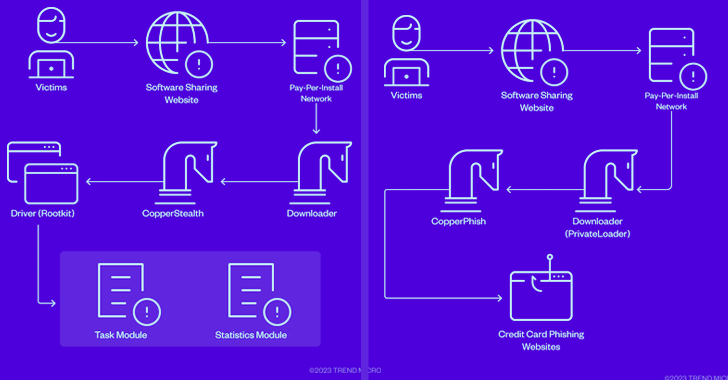
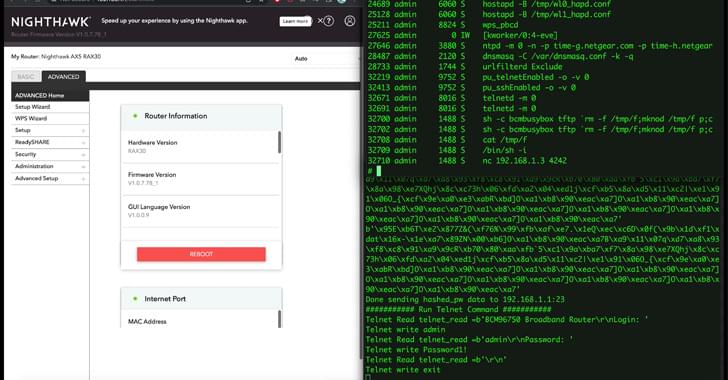
Distributed denial-of-service (DDoS) attacks are growing in frequency and sophistication, thanks to the number of attack tools available for a couple of dollars on the Dark Web and criminal marketplaces. Numerous organizations became victims in 2022, from the Port of London Authority to Ukraine’s national postal service.
Security leaders are already combating DDoS attacks by monitoring network traffic patterns, implementing firewalls, and using content delivery networks (CDNs) to distribute traffic across multiple servers. But putting more security controls in place can also result in more DDoS false positives — legitimate traffic that’s not part of an attack but still requires analysts to take steps to mitigate before it causes service disruptions and brand damage.
Rate limiting is often considered the best method for efficient DDoS mitigation: URL-specific rate limiting prevents 47% of DDoS attacks, according to Indusface’s “State of Application Security Q4 2022” report. However, the reality is that few engineering leaders know how to use it effectively. Here’s how to employ rate limiting effectively while avoiding false positives.