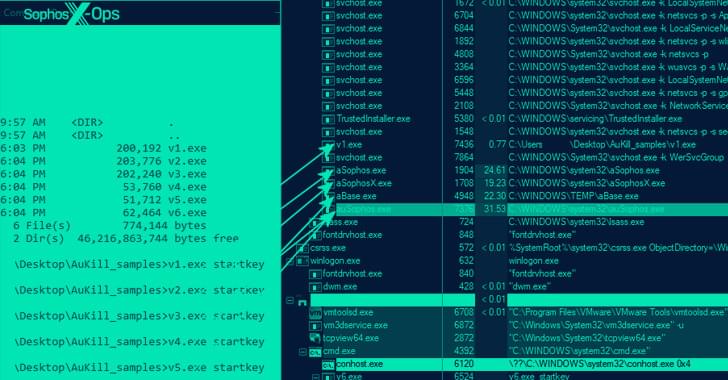
Play ransomware is notable for not only utilizing intermittent encryption to speed up the process, but also for the fact that it’s not operated on a ransomware-as-a-service (RaaS) model. Evidence gathered so far points to Balloonfly carrying out the ransomware attacks as well as developing the malware themselves.
Grixba and VSS Copying Tool are the latest in a long list of proprietary tools such as Exmatter, Exbyte, and PowerShell-based scripts that are used by ransomware actors to establish more control over their operations, while also adding extra layers of complexity to persist in compromised environments and evade detection.
Another technique increasingly adopted by financially-motivated groups is the use of the Go programming language to develop cross-platform malware and resist analysis and reverse engineering efforts.