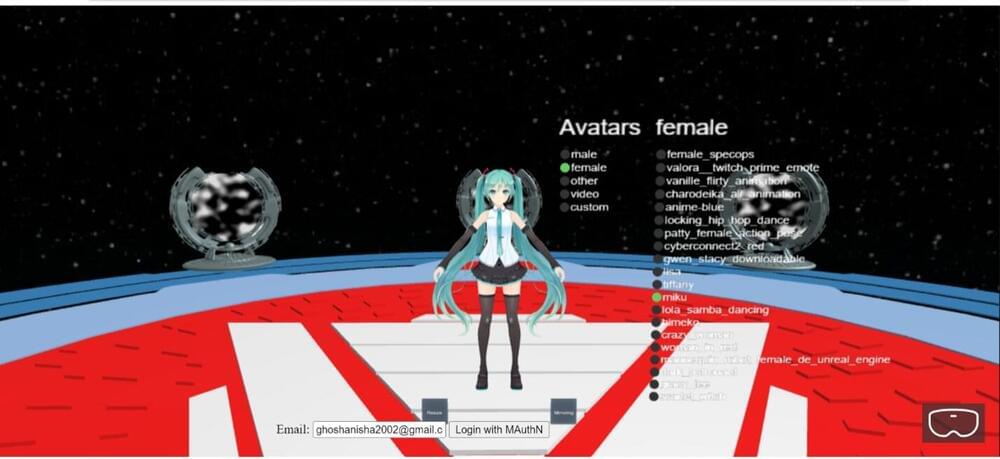
In recent years, many computer scientists have been exploring the notion of metaverse, an online space in which users can access different virtual environments and immersive experiences, using VR and AR headsets. While navigating the metaverse, users might also share personal data, whether to purchase goods, connect with other users, or for other purposes.
Past studies have consistently highlighted the limitations of password authentication systems, as there are now many cyber-attacks and strategies for cracking them. To increase the security of users navigating the metaverse, therefore, password-based authentication would be far from ideal.
This inspired a team of researchers at VIT-AP University in India to create MetaSecure, a password-less authentication system for the metaverse. This system, introduced in a paper pre-published on arXiv, combines three different authentication techniques, namely device attestation, facial recognition and physical security keys.