INTERPOL’s Operation Sentinel led to 574 arrests, $3M recovered, and major ransomware and fraud disruptions across 19 African countries.



The WebRAT malware is now being distributed through GitHub repositories that claim to host proof-of-concept exploits for recently disclosed vulnerabilities.
Previously spread through pirated software and cheats for games like Roblox, Counter Strike, and Rust, WebRAT is a backdoor with info-stealing capabilities that emerged at the beginning of the year.
According to a report from Solar 4RAYS in May, WebRAT can steal credentials for Steam, Discord, and Telegram accounts, as well as cryptocurrency wallet data. It can also spy on victims through webcams and capture screenshots.

#neuromorphic #computing #futuretech
By Chuck Brooks, Skytop Contributor / December 3, 2025
Chuck Brooks serves as President and Consultant of Brooks Consulting International. Chuck also serves as an Adjunct Professor at Georgetown University in the Cyber Risk Management Program, where he teaches graduate courses on risk management, homeland security, and cybersecurity.
Chuck has received numerous global accolades for his work and promotion of cybersecurity. Recently, he was named the top cybersecurity expert to follow on social media, and also as one top cybersecurity leaders for 2024. He has also been named “Cybersecurity Person of the Year” by Cyber Express, Cybersecurity Marketer of the Year, and a “Top 5 Tech Person to Follow” by LinkedIn” where he has 120,000 followers on his profile.
As a thought leader, blogger, and event speaker, he has briefed the G20 on energy cybersecurity, The US Embassy to the Holy See, and the Vatican on global cybersecurity cooperation. He has served on two National Academy of Science Advisory groups, including one on digitalizing the USAF, and another on securing BioTech. He has also addressed USTRANSCOM on cybersecurity and serves on an industry/government Working group for DHS CISA focused on security space systems.


Nissan Motor Co. Ltd. (Nissan) has confirmed that information of thousands of its customers has been compromised after the data breach at Red Hat in September.
The Japanese multinational automobile manufacturer headquartered in Yokohama, Japan, produces more than 3.2 million cars a year. The company employs 120,000 people and has a strong presence in Japan, North America, Europe, and Asia.
In an announcement yesterday, Nissan informed that it was indirectly impacted by a security breach incident at the U.S.-based enterprise software company Red Hat.

The latest variant of the MacSync information stealer targeting macOS systems is delivered through a digitally signed, notarized Swift application.
Security researchers at Apple device management platform Jamf say that the distribution method constitutes a significant evolution from past iterations that used less sophisticated “drag-to-Terminal” or ClickFix tactics.
“Delivered as a code-signed and notarized Swift application within a disk image named zk-call-messenger-installer-3.9.2-lts.dmg, distributed via https://zkcall.net/download, it removes the need for any direct terminal interaction,” the researchers say in a report today.

An Interpol-coordinated initiative called Operation Sentinel led to the arrest of 574 individuals and the recovery of $3 million linked to business email compromise, extortion, and ransomware incidents.
Between October 27 and November 27, the investigation, which involved law enforcement in 19 countries, took down more than 6,000 malicious links and decrypted six distinct ransomware variants.
Interpol says that the cybercrime cases investigated are connected to more than $21 million in financial losses.

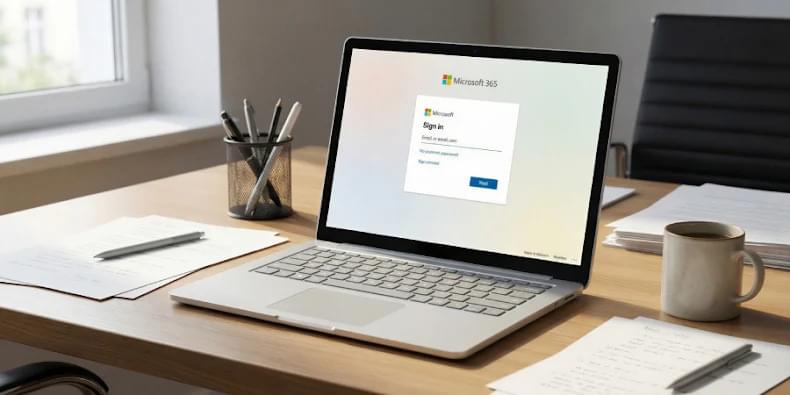
A suspected Russia-aligned group has been attributed to a phishing campaign that employs device code authentication workflows to steal victims’ Microsoft 365 credentials and conduct account takeover attacks.
The activity, ongoing since September 2025, is being tracked by Proofpoint under the moniker UNK_AcademicFlare.
The attacks involve using compromised email addresses belonging to government and military organizations to strike entities within government, think tanks, higher education, and transportation sectors in the U.S. and Europe.
