Sneaky 2FA adds BitB phishing and attackers exploit passkey flaws using rogue extensions and downgrade attacks.



A global campaign dubbed ShadowRay 2.0 hijacks exposed Ray Clusters by exploiting an old code execution flaw to turn them into a self-propagating cryptomining botnet.
Developed by Anyscale, the Ray open-source framework allows building and scaling AI and Python applications in a distributed computing ecosystem organized in clusters, or head nodes.
According to researchers at runtime security company Oligo, a threat actor they track as IronErn440 is using AI-generated payloads to compromise vulnerable Ray infrastructure that is reachable over the public internet.
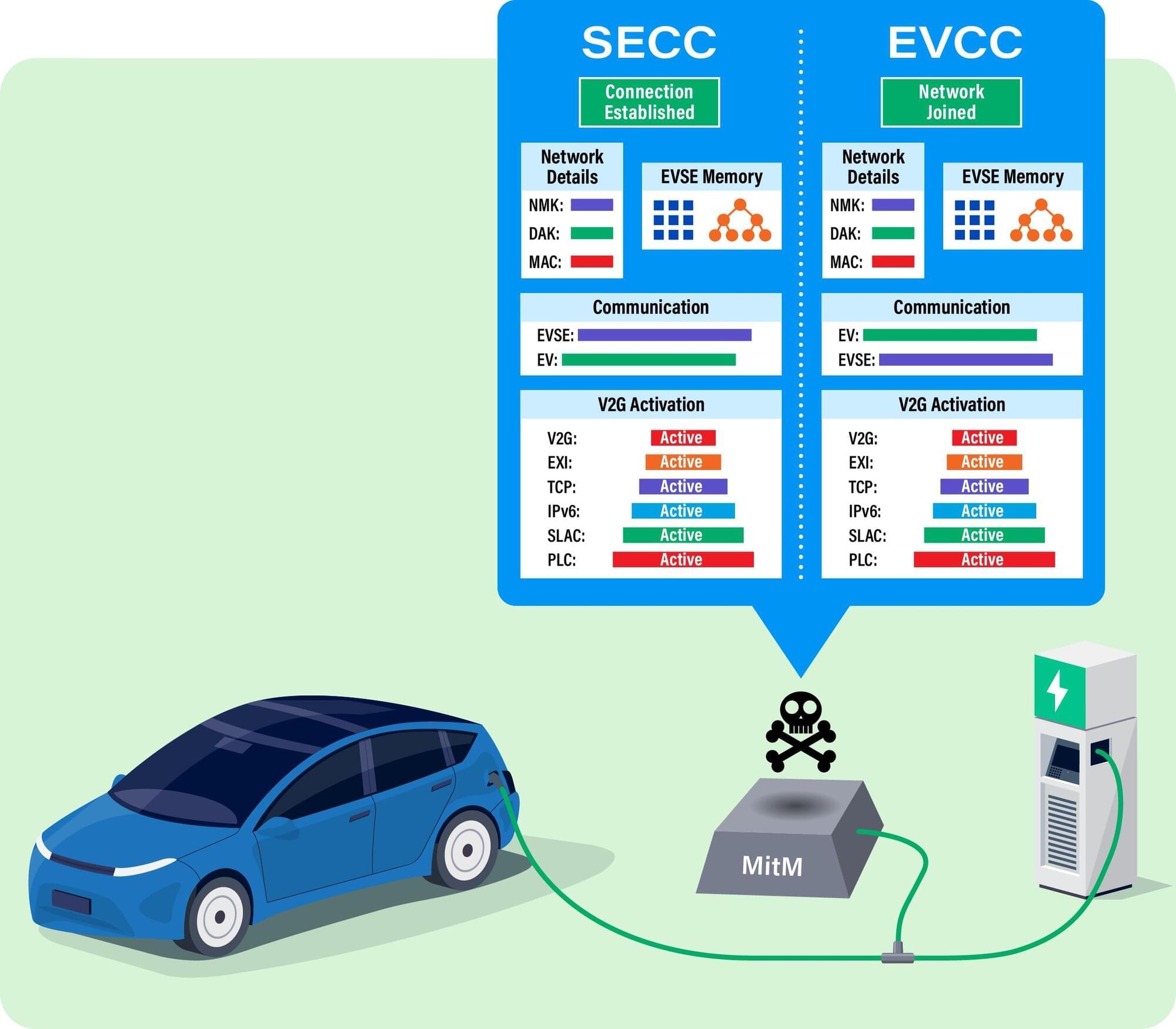
Southwest Research Institute identified a security vulnerability in a standard protocol governing communications between electric vehicles (EV) and EV charging equipment. The research prompted the Cybersecurity & Infrastructure Security Agency (CISA) to issue a security advisory related to the ISO 15118 vehicle-to-grid communications standard.


The decades-old “finger” command is making a comeback„ with threat actors using the protocol to retrieve remote commands to execute on Windows devices.
In the past, people used the finger command to look up information about local and remote users on Unix and Linux systems via the Finger protocol, a command later added to Windows. While still supported, it’s rarely used today compared to its popularity decades ago.
When executed, the finger command returns basic information about a user, including their login name, name (if set in /etc/passwd), home directory, phone numbers, last seen, and other details.

IronSource Expands Samsung Partnership, Launching on Samsung Mobile Devices in MENA https://www.businesswire.com/news/home/20221103005106/en/iro…es-in-MENA
Across West Asia and North Africa (WANA), growing concerns about digital surveillance have placed Israeli cybersecurity firms and their software under intense scrutiny. Among the most alarming cases is AppCloud, a pre-installed application on Samsung’s A and M series smartphones.
The bloatware cannot be uninstalled easily because it runs on the device’s operating system. Uninstalling it requires root access (the highest level of control in a computer system) of the phone to remove the AppCloud package. Its privacy policy is nowhere to be found online and opting out is not always available.
But the real concern lies in who owns AppCloud. When investigating further, we discovered that AppCloud’s privacy policy can be traced back to the controversial Israeli-founded company ironSource (now owned by the American company Unity). ironSource is notorious for its questionable practices regarding user consent and data privacy.


Google is backpedaling on its decision to introduce new identity verification rules for all developers, stating that it will also introduce accounts for limited app distribution and will allow users to install apps from unverified devs.
As announced in August, Google was planning to introduce what it called “Developer Verification” starting in 2026 to block malware spreading via sideloaded apps sourced from outside the official Google Play app store.
The new rules require that all apps must originate from developers with verified identities to be installed on certified Android devices; otherwise, their installation will be blocked.