Researchers expose new WordPress malware and ClickFix phishing kits exploiting cache smuggling for stealth attacks.
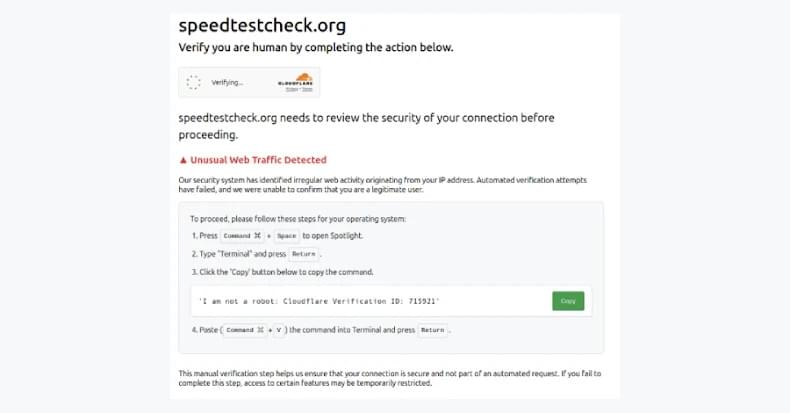


A new variant of the FileFix social engineering attack uses cache smuggling to secretly download a malicious ZIP archive onto a victim’s system and bypassing security software.
The new phishing and social engineering attack impersonates a “Fortinet VPN Compliance Checker” and was first spotted by cybersecurity researcher P4nd3m1cb0y, who shared information about it on X.
In a new report by cybersecurity firm Expel, cybersecurity researcher Marcus Hutchins shares more details on how this attack works.

Nowadays data breaches aren’t rare shocks—they’re a weekly drumbeat. From leaked customer records to stolen source code, our digital lives keep spilling into the open.
Git services are especially vulnerable to cybersecurity threats. These are online hosting platforms that are widely used in the IT industry to collaboratively develop software, and are home to most of the world’s computer code.
Just last week, hackers reportedly stole about 570 gigabytes of data from a git service called GitLab. The stolen data was associated with major companies such as IBM and Siemens, as well as United States government organizations.

Researchers from NC State University have identified the first hardware vulnerability that allows attackers to compromise the data privacy of artificial intelligence (AI) users by exploiting the physical hardware on which AI is run.
The paper, “GATEBLEED: A Timing-Only Membership Inference Attack, MoE-Routing Inference, and a Stealthy, Generic Magnifier Via Hardware Power Gating in AI Accelerators,” will be presented at the IEEE/ACM International Symposium on Microarchitecture (MICRO 2025), being held Oct. 18–22 in Seoul, South Korea. The paper is currently available on the arXiv preprint server.
“What we’ve discovered is an AI privacy attack,” says Joshua Kalyanapu, first author of a paper on the work and a Ph.D. student at North Carolina State University. “Security attacks refer to stealing things actually stored somewhere in a system’s memory—such as stealing an AI model itself or stealing the hyperparameters of the model. That’s not what we found. Privacy attacks steal stuff not actually stored on the system, such as the data used to train the model and attributes of the data input to the model. These facts are leaked through the behavior of the AI model. What we found is the first vulnerability that allows successfully attacking AI privacy via hardware.”

Fooled into following a hacker’s rogue commands, a drone is liable to do any number of things. Fly erratically. Speed up. Slow down. Hang suspended in the air. Reverse course. Take a new course. And, most dangerously: Crash.
What the compromised drone cannot do, however, is regain control. Lost to its original assignment—whether it’s delivering a package, inspecting an aging bridge or monitoring the health of crops—the machine is essentially useless.
At FIU, cybersecurity researchers have developed a series of countermeasures to fight back mid-flight against hostile takeovers.

In October 2024, Cyble also disclosed details of a sophisticated multi-stage attack campaign orchestrated by a Vietnamese threat actor that targeted job seekers and digital marketing professionals with Quasar RAT using phishing emails containing booby-trapped job description files.
BatShadow is assessed to be active for at least a year, with prior campaigns using similar domains, such as samsung-work[.]com, to propagate malware families including Agent Tesla, Lumma Stealer, and Venom RAT.
“The BatShadow threat group continues to employ sophisticated social engineering tactics to target job seekers and digital marketing professionals,” Aryaka said. “By leveraging disguised documents and a multi-stage infection chain, the group delivers a Go-based Vampire Bot capable of system surveillance, data exfiltration, and remote task execution.”



Introduction.
Grounded in the scientific method, it critically examines the work’s methodology, empirical validity, broader implications, and opportunities for advancement, aiming to foster deeper understanding and iterative progress in quantum technologies. ## Executive Summary.
This work, based on experiments conducted in 1984–1985, addresses a fundamental question in quantum physics: the scale at which quantum effects persist in macroscopic systems.
By engineering a Josephson junction-based circuit where billions of Cooper pairs behave collectively as a single quantum entity, the laureates provided empirical evidence that quantum phenomena like tunneling through energy barriers and discrete energy levels can manifest in human-scale devices.
This breakthrough bridges microscopic quantum mechanics with macroscopic engineering, laying foundational groundwork for advancements in quantum technologies such as quantum computing, cryptography, and sensors.
Overall strengths include rigorous experimental validation and profound implications for quantum information science, though gaps exist in scalability to room-temperature applications and full mitigation of environmental decoherence.
Framed within the broader context, this award highlights the enduring evolution of quantum mechanics from theoretical curiosity to practical innovation, building on prior Nobel-recognized discoveries like the Josephson effect (1973) and superconductivity mechanisms (1972).

Enterprise software giant Red Hat is now being extorted by the ShinyHunters gang, with samples of stolen customer engagement reports (CERs) leaked on their data leak site.
News of the Red Hat data breach broke last week when a hacking group known as the Crimson Collective claimed to have stolen nearly 570GB of compressed data across 28,000 internal development repositories.
This data allegedly includes approximately 800 Customer Engagement Reports (CERs), which can contain sensitive information about a customer’s network, infrastructure, and platforms.