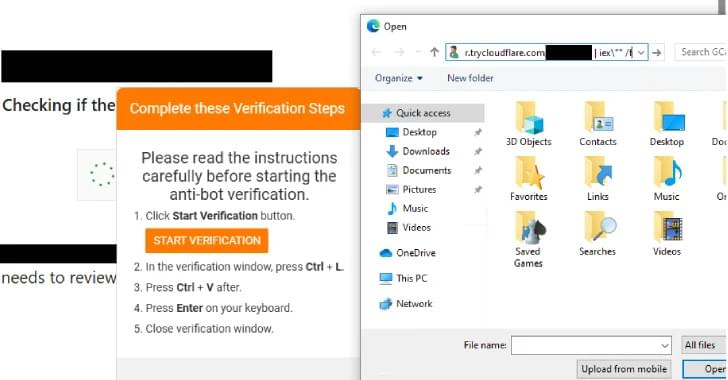
A new variant of the Konfety Android malware emerged with a malformed ZIP structure along with other obfuscation methods that allow it to evade analysis and detection.
Konfety poses as a legitimate app, mimicking innocuous products available on Google Play, but features none of the promised functionality.
The capabilities of the malware include redirecting users to malicious sites, pushing unwanted app installs, and fake browser notifications.