APT36 spoofed India Post using malware-laced PDFs and Android apps to harvest sensitive data.




The legacy domain for Microsoft Stream was hijacked to show a fake Amazon site promoting a Thailand casino, causing all SharePoint sites with old embedded videos to display it as spam.
Microsoft Stream is an enterprise video streaming service that allows organizations to upload and share videos in Microsoft 365 apps, such as Teams and SharePoint.
Video content hosted on Microsoft Stream was accessed or embedded through a portal at microsoftstream.com.
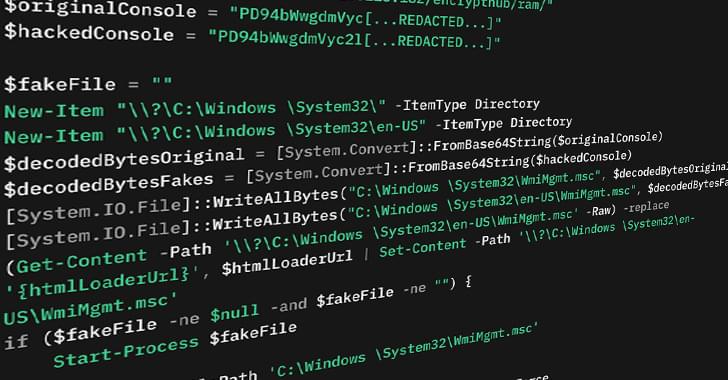
The threat actor known as EncryptHub exploited a recently-patched security vulnerability in Microsoft Windows as a zero-day to deliver a wide range of malware families, including backdoors and information stealers such as Rhadamanthys and StealC.
“In this attack, the threat actor manipulates.msc files and the Multilingual User Interface Path (MUIPath) to download and execute malicious payload, maintain persistence and steal sensitive data from infected systems,” Trend Micro researcher Aliakbar Zahravi said in an analysis.
The vulnerability in question is CVE-2025–26633 (CVSS score: 7.0), described by Microsoft as an improper neutralization vulnerability in Microsoft Management Console (MMC) that could allow an attacker to bypass a security feature locally. It was fixed by the company earlier this month as part of its Patch Tuesday update.

Such credentials could be obtained from a data breach of a social media service or be acquired from underground forums where they are advertised for sale by other threat actors.
Credential stuffing is also different from brute-force attacks, which revolve around cracking passwords, login credentials, and encryption keys using a trial and error method.
Atlantis AIO, per Abnormal Security, offers threat actors the ability to launch credential stuffing attacks at scale via pre-configured modules for targeting a range of platforms and cloud-based services, thereby facilitating fraud, data theft, and account takeovers.



A major telecommunications company located in Asia was allegedly breached by Chinese state-sponsored hackers who spent over four years inside its systems, according to a new report from incident response firm Sygnia.
The cybersecurity company is tracking the activity under the name Weaver Ant, describing the threat actor as stealthy and highly persistent. The name of the telecom provider was not disclosed.
“Using web shells and tunneling, the attackers maintained persistence and facilitated cyber espionage,” Sygnia said. “The group behind this intrusion […] aimed to gain and maintain continuous access to telecommunication providers and facilitate cyber espionage by collecting sensitive information.”

Law enforcement authorities in seven African countries have arrested 306 suspects and confiscated 1,842 devices as part of an international operation codenamed Red Card that took place between November 2024 and February 2025.
The coordinated effort “aims to disrupt and dismantle cross-border criminal networks which cause significant harm to individuals and businesses,” INTERPOL said, adding it focused on targeted mobile banking, investment, and messaging app scams.
The cyber-enabled scams involved more than 5,000 victims. The countries that participated in the operation include Benin, Côte d’Ivoire, Nigeria, Rwanda, South Africa, Togo, and Zambia.