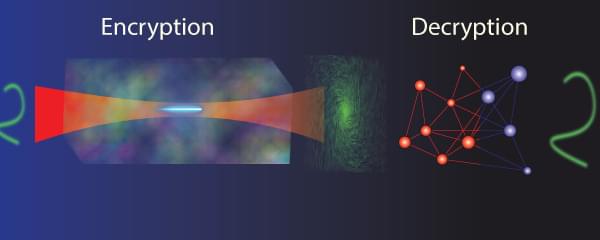
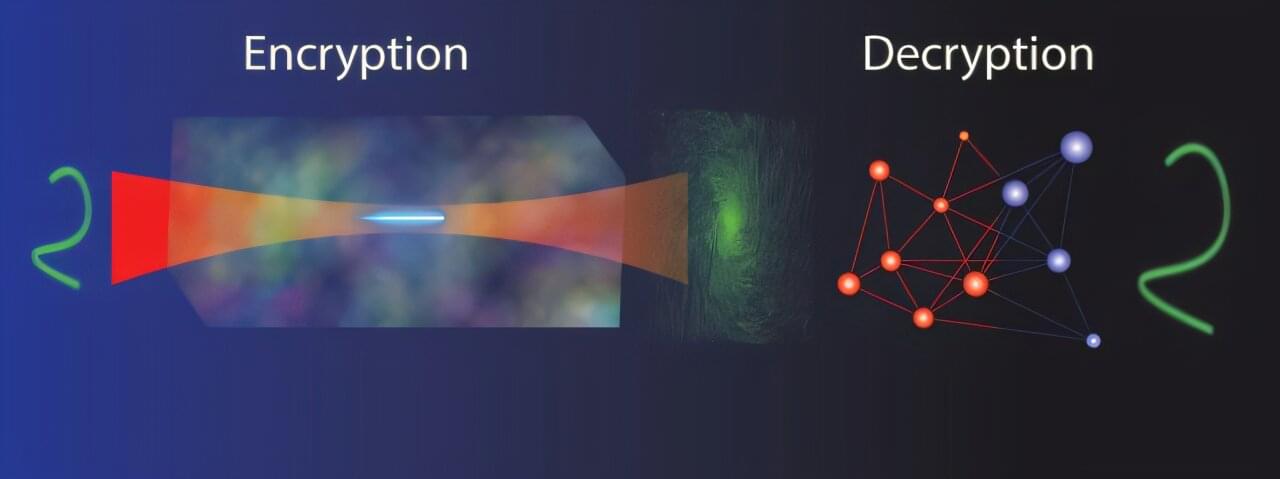
WASHINGTON — As the demand for digital security grows, researchers have developed a new optical system that uses holograms to encode information, creating a level of encryption that traditional methods cannot penetrate. This advance could pave the way for more secure communication channels, helping to protect sensitive data.
“From rapidly evolving digital currencies to governance, healthcare, communications and social networks, the demand for robust protection systems to combat digital fraud continues to grow,” said research team leader Stelios Tzortzakis from the Institute of Electronic Structure and Laser, Foundation for Research and Technology Hellas and the University of Crete, both in Greece.
Optica is the leading society in optics and photonics. Quality information and inspiring interactions through publications, meetings, and membership.