In recent years, quantum physicists and engineers have been trying to develop quantum computer processors that perform better than classical computers on some tasks. Yet conclusive demonstrations proving that quantum systems perform better than their classical counterparts (i.e., realizations of a quantum advantage) remain scarce, due to various experimental challenges.
Researchers at Henan Key Laboratory of Quantum Information and Cryptography and the S. N. Bose National Center for Basic Sciences carried out an experiment aimed at establishing the quantum advantage of an elementary quantum system for information storage.
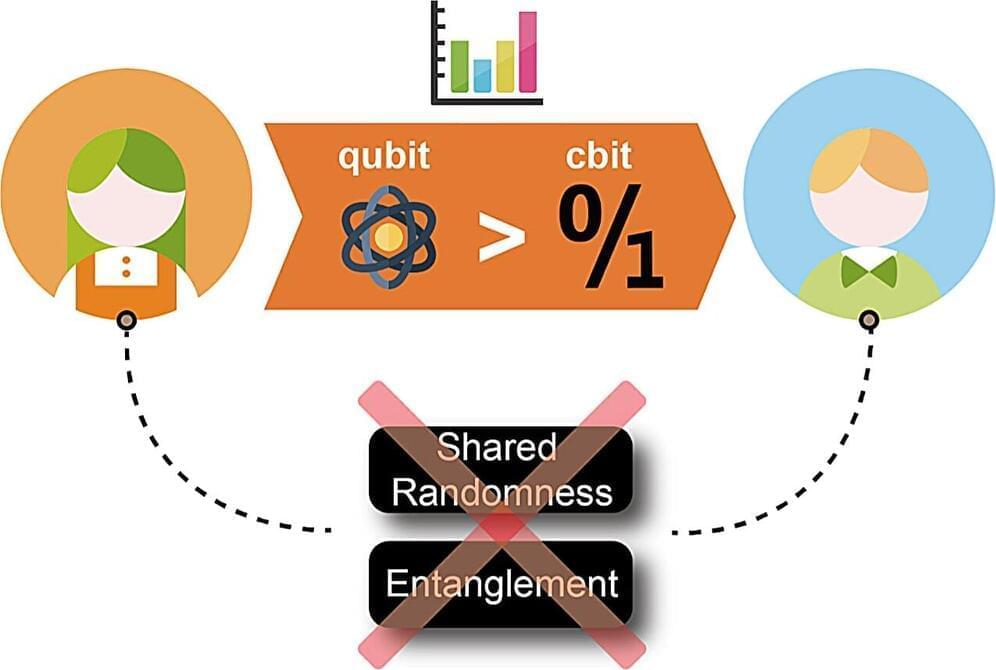
Their paper, published in Physical Review Letters, demonstrates that a single qubit can outperform a classical bit in a communication task that does not involve any shared randomness (i.e., classically correlated random variables between communicating parties).