Quantum computers will break encryption one day. But converting data into light particles and beaming them around using thousands of satellites might be one way around this problem.


The development of Transhumanism / Extropianism in the final two decades of the 20th century also set in motion the creation of digital cash, including the breakthrough killer app: Bitcoin.
The Austrian economist Friedrich Hayek wanted to denationalize money. David Chaum, an innovator in the field of cryptography and electronic cash, wanted to shield it from surveillance. Their goals were not the same, but they each inspired the same man.
Max O’Connor grew up in the British city of Bristol in the 1960s and ’70s. Telling his life story to Wired in 1994, he explained how he had always dreamed of a future where humanity expanded its potential in science-fictional ways, a world where people would possess X-ray vision, carry disintegrator guns, or walk straight through walls.
By his teenage years, O’Connor had acquired an interest in the occult. He thought the key to realizing superhuman potential could perhaps be found in the same domain as astral projection, dowsing rods, and reincarnation. But he began to realize there was no compelling evidence that any of these mystical practices actually worked. Human progress, he soon decided, was best served not by the supernatural but by science and logic.
All non-Google chat GPTs affected by side channel that leaks responses sent to users.

A team of Chinese scientists introduced a quantum communication technique that they say could help secure Web 3.0 against the formidable threat of quantum computing.
Their approach, called Long-Distance Free-Space Quantum Secure Direct Communication (LF QSDC), promises to improve data security by enabling encrypted direct messaging without the need for key exchange, a method traditionally vulnerable to quantum attacks.
They add the approach not only enhances security but also aligns with the decentralized ethos of Web 3.0, offering a robust defense in the rapidly evolving digital landscape.

Creating a quantum computer powerful enough to tackle problems we cannot solve with current computers remains a big challenge for quantum physicists. A well-functioning quantum simulator – a specific type of quantum computer – could lead to new discoveries about how the world works at the smallest scales. Quantum scientist Natalia Chepiga from Delft University of Technology has developed a guide on how to upgrade these machines so that they can simulate even more complex quantum systems. The study is now published in Physical Review Letters.
“Creating useful quantum computers and quantum simulators is one of the most important and debated topics in quantum science today, with the potential to revolutionize society,” says researcher Natalia Chepiga. Quantum simulators are a type of quantum computer, Chepiga explains: “Quantum simulators are meant to address open problems of quantum physics to further push our understanding of nature. Quantum computers will have wide applications in various areas of social life, for example in finances, encryption, and data storage.”
Steering Wheel
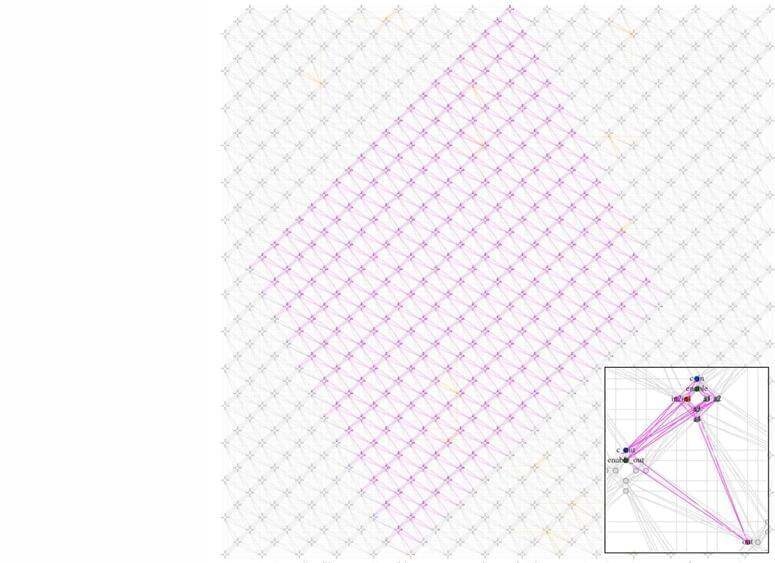
Researchers at the University of Trento, Italy, have developed a novel approach for prime factorization via quantum annealing, leveraging a compact modular encoding paradigm and enabling the factorization of large numbers using D-Wave quantum devices.
Prime factorization is the procedure of breaking down a number into its prime components. Every integer greater than one can be uniquely expressed as a product of prime numbers.
In cryptography, prime factorization holds particular importance due to its relevance to the security of encryption algorithms, such as the widely used RSA cryptosystem.
Creating a quantum computer powerful enough to tackle problems we cannot solve with current computers remains a big challenge for quantum physicists. A well-functioning quantum simulator—a specific type of quantum computer—could lead to new discoveries about how the world works at the smallest scales.
Quantum scientist Natalia Chepiga from Delft University of Technology has developed a guide on how to upgrade these machines so that they can simulate even more complex quantum systems. The study is now published in Physical Review Letters.
“Creating useful quantum computers and quantum simulators is one of the most important and debated topics in quantum science today, with the potential to revolutionize society,” says researcher Natalia Chepiga. Quantum simulators are a type of quantum computer. Chepiga explains, “Quantum simulators are meant to address open problems of quantum physics to push our understanding of nature further. Quantum computers will have wide applications in various areas of social life, for example, in finances, encryption, and data storage.”

Big Tech is also throwing its weight behind a promising technical standard that could add a “nutrition label” to images, video, and audio. Called C2PA, it’s an open-source internet protocol that relies on cryptography to encode details about the origins of a piece of content, or what technologists refer to as “provenance” information. The developers of C2PA often compare the protocol to a nutrition label, but one that says where content came from and who—or what—created it. Read more about it here.
On February 8, Google announced it is joining other tech giants such as Microsoft and Adobe in the steering committee of C2PA and will include its watermark SynthID in all AI-generated images in its new Gemini tools. Meta says it is also participating in C2PA. Having an industry-wide standard makes it easier for companies to detect AI-generated content, no matter which system it was created with.
OpenAI too announced new content provenance measures last week. It says it will add watermarks to the metadata of images generated with ChatGPT and DALL-E 3, its image-making AI. OpenAI says it will now include a visible label in images to signal they have been created with AI.

Quantum physicist Mickael Perrin uses graphene ribbons to build nanoscale power plants that turn waste heat from electrical equipment into electricity.
When Mickael Perrin started out on his scientific career 12 years ago, he had no way of knowing he was conducting research in an area that would be attracting wide public interest only a few years later: quantum electronics.
“At the time, physicists were just starting to talk about the potential of quantum technologies and quantum computers,” he recalls. “Today there are dozens of start-ups in this area, and governments and companies are investing billions in developing the technology further. We are now seeing the first applications in computer science, cryptography, communications, and sensors.”