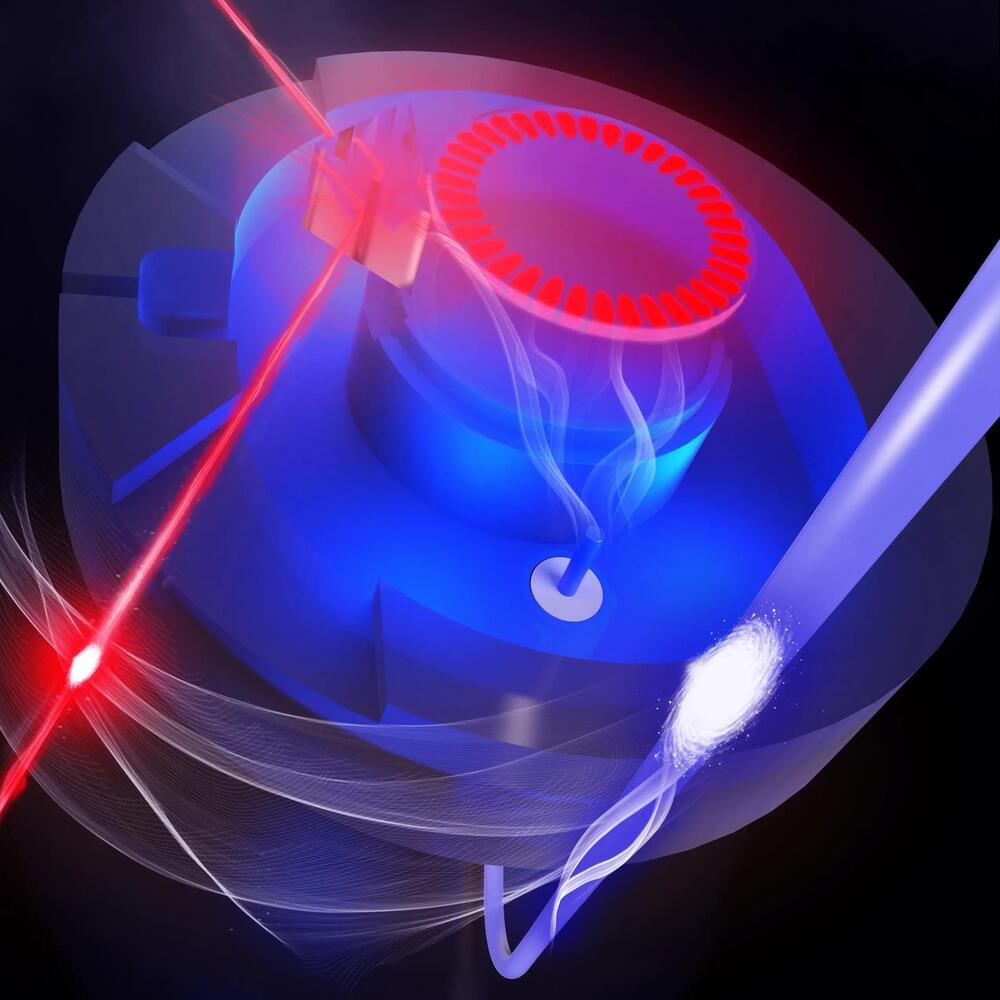
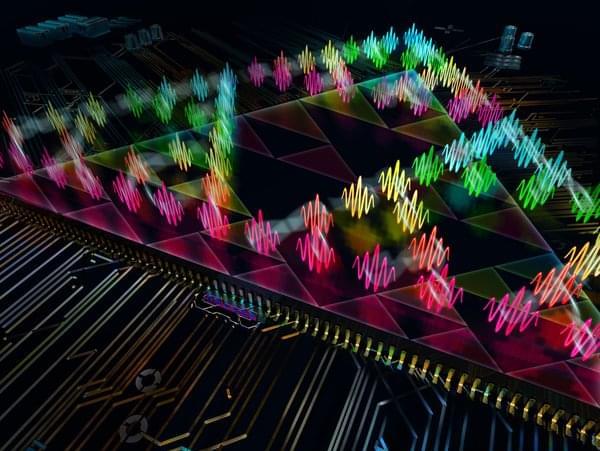
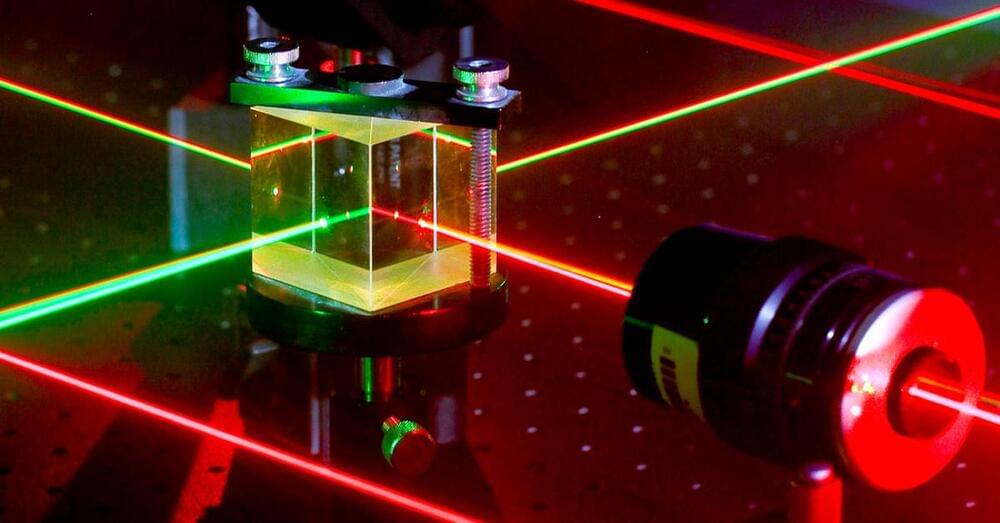
Basic, or “elementary,” cellular automata like The Game of Life appeal to researchers working in mathematics and computer science theory, but they can have practical applications too. Some of the elementary cellular automata can be used for random number generation, physics simulations, and cryptography. Others are computationally as powerful as conventional computing architectures—at least in principle. In a sense, these task-oriented cellular automata are akin to an ant colony in which the simple actions of individual ants combine to perform larger collective actions, such as digging tunnels, or collecting food and taking it back to the nest. More “advanced” cellular automata, which have more complicated rules (although still based on neighboring cells), can be used for practical computing tasks such as identifying objects in an image.
Marandi explains: “While we are fascinated by the type of complex behaviors that we can simulate with a relatively simple photonic hardware, we are really excited about the potential of more advanced photonic cellular automata for practical computing applications.”
Marandi says cellular automata are well suited to photonic computing for a couple of reasons. Since information processing is happening at an extremely local level (remember in cellular automata, cells interact only with their immediate neighbors), they eliminate the need for much of the hardware that makes photonic computing difficult: the various gates, switches, and devices that are otherwise required for moving and storing light-based information. And the high-bandwidth nature of photonic computing means cellular automata can run incredibly fast. In traditional computing, cellular automata might be designed in a computer language, which is built upon another layer of “machine” language below that, which itself sits atop the binary zeroes and ones that make up digital information.