Quantum bits inspired by Schrödinger’s cat could allow quantum computers to make fewer mistakes and more efficiently crack algorithms used for encryption.
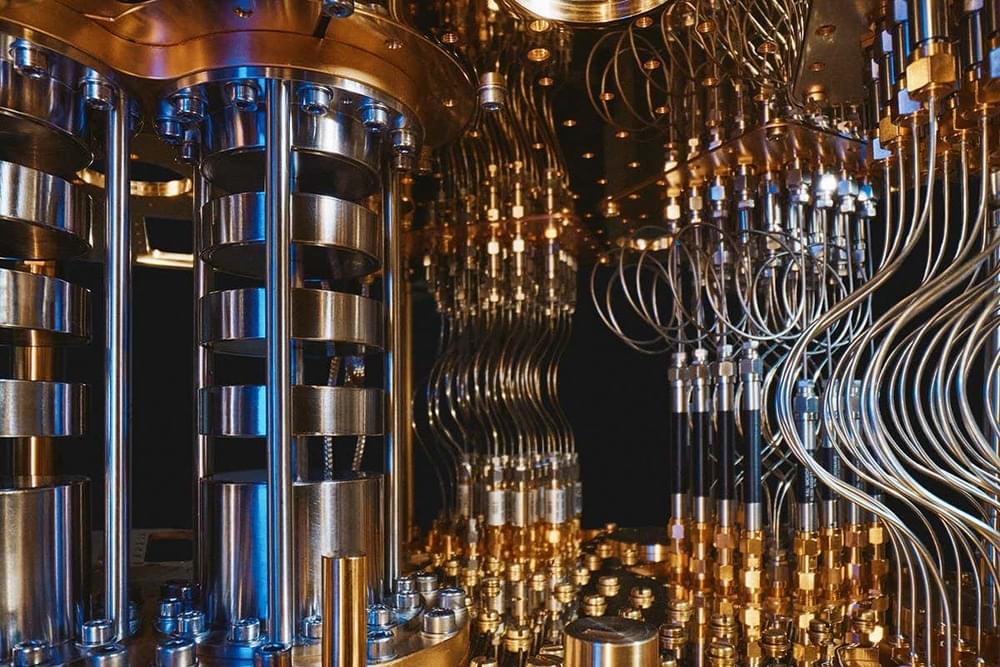

Quantum bits inspired by Schrödinger’s cat could allow quantum computers to make fewer mistakes and more efficiently crack algorithms used for encryption.

Founder of Intellisystem Technologies. Scientific researcher and professor at eCampus University. NASA Genelab AWG AI/ML member.
Quantum computing is a new approach founded on quantum mechanics principles to perform calculations. Unlike classical computers, which store information in bits (either 0 or 1), quantum computers use quantum bits or “qubits” that can exist in multiple states simultaneously. This physics property allows quantum computers to perform specific calculations much faster than classical computers.
The potential applications of quantum computing are vast and include fields such as cryptography, finance and drug discovery. It promises to transform multiple industries and tackle challenges that classical computers cannot solve.

Already smarting from a breach that put partially encrypted login data into a threat actor’s hands, LastPass on Monday said that the same attacker hacked an employee’s home computer and obtained a decrypted vault available to only a handful of company developers.
Although an initial intrusion into LastPass ended on August 12, officials with the leading password manager said the threat actor “was actively engaged in a new series of reconnaissance, enumeration, and exfiltration activity” from August 12 to August 26. In the process, the unknown threat actor was able to steal valid credentials from a senior DevOps engineer and access the contents of a LastPass data vault. Among other things, the vault gave access to a shared cloud-storage environment that contained the encryption keys for customer vault backups stored in Amazon S3 buckets.

The buzz in the wireless industry is all about space, or what is referred to as non-terrestrial networks (NTNs). The wireless 3GPP Release 17 specification includes two new standards for satellite communications from smartphones, mobile electronics, and IoT devices directly to satellites. While satellites have always been part of the wireless communications infrastructure, they have traditionally provided backhaul network communications, not direct communications to mobile devices other than clunky satellite phones and emergency equipment. Direct satellite communications with individual mobile devices will help overcome gaps in terrestrial cellular networks, providing a truly global infrastructure that can be leveraged by a variety of industries, and bridge the digital divide by bringing wireless communications to rural areas that often lack the infrastructure even with the rollout of 5G cellular networks.
The 3rd Generation Partnership Project or 3GPP is a global standards body consisting of a wide variety of wireless ecosystem members, such as intellectual property (IP) providers, semiconductor companies, networking companies, device OEMs, and wireless operators. Since 1998 and 2G cellular technology, members of the 3GPP have worked together to develop standards for new wireless technologies continuously. While the industry is now well past 3G and new generations of cellular technology are still introduced approximately every 10 years, new releases of the 3GPP standards are released approximately every two years within a generation in an on-going effort to increase the efficient use of a limited natural resource – radio spectrum. The standards also encourage the freeing up of additional spectrum, the development of new radio access networks (RANs), new encryption technology, higher network performance, aggregation of spectrum from different carriers and wireless technologies, support for additional use cases, and new network configurations. In other words, the 3GPP group is tasked with improving wireless technology with each generation and providing a global network that can be accessed from anywhere and by any device. With the inclusion of satellite networks, or non-terrestrial networks (NTNs), a global network will finally be possible.
The latest 3GPP standard that was finalized in 2023 is Release 17, the 3rd Release within the 5G cellular generation. Among other enhancements and additions, Release 17 includes two new standards for satellite networks, IoT-NTN and New Radio NTN or NR-NTN. The IoT-NTN standard defines narrow band using a 200KHz channel for two-way messaging and other low-bandwidth consumer and embedded/IoT applications, such as location tracking, asset tracking, and sensor monitoring. The data rates for IoT-NTN are similar to the data rates that were experienced in 2G. It will provide basic data connectivity.

The CRYSTALS-Kyber public-key encryption and key encapsulation mechanism recommended by NIST in July 2022 for post-quantum cryptography has been broken. Researchers from the KTH Royal Institute of Technology, Stockholm, Sweden, used recursive training AI combined with side channel attacks.
A side-channel attack exploits measurable information obtained from a device running the target implementation via channels such as timing or power consumption. The revolutionary aspect of the research (PDF) was to apply deep learning analysis to side-channel differential analysis.
“Deep learning-based side-channel attacks,” say the researchers, “can overcome conventional countermeasures such as masking, shuffling, random delays insertion, constant-weight encoding, code polymorphism, and randomized clock.”
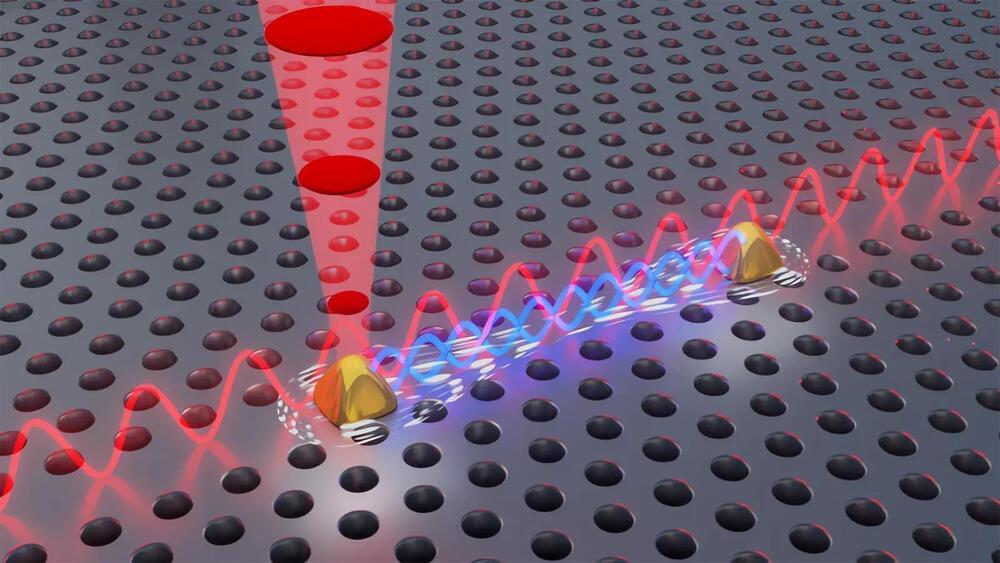
In a new breakthrough, researchers at the University of Copenhagen, in collaboration with Ruhr University Bochum, have solved a problem that has caused quantum researchers headaches for years. The researchers can now control two quantum light sources rather than one. Trivial as it may seem to those uninitiated in quantum, this colossal breakthrough allows researchers to create a phenomenon known as quantum mechanical entanglement. This, in turn, opens new doors for companies and others to exploit the technology commercially.
Going from one to two is a minor feat in most contexts. But in the world of quantum physics, doing so is crucial. For years, researchers around the world have strived to develop stable quantum light sources and achieve the phenomenon known as quantum mechanical entanglement – a phenomenon, with nearly sci-fi-like properties, where two light sources can affect each other instantly and potentially across large geographic distances. Entanglement is the very basis of quantum networks and central to the development of an efficient quantum computer.
Researchers from the Niels Bohr Institute published a new result in the highly esteemed journal Science, in which they succeeded in doing just that. According to Professor Peter Lodahl, one of the researchers behind the result, it is a crucial step in the effort to take the development of quantum technology to the next level and to “quantize” society’s computers, encryption, and the internet.
A second problem is the risk of technological job loss. This is not a new worry; people have been complaining about it since the loom, and the arguments surrounding it have become stylized: critics are Luddites who hate progress. Whither the chandlers, the lamplighters, the hansom cabbies? When technology closes one door, it opens another, and the flow of human energy and talent is simply redirected. As Joseph Schumpeter famously said, it is all just part of the creative destruction of capitalism. Even the looming prospect of self-driving trucks putting 3.5 million US truck drivers out of a job is business as usual. Unemployed truckers can just learn to code instead, right?
Those familiar replies make sense only if there are always things left for people to do, jobs that can’t be automated or done by computers. Now AI is coming for the knowledge economy as well, and the domain of humans-only jobs is dwindling absolutely, not merely morphing into something new. The truckers can learn to code, and when AI takes that over, coders can… do something or other. On the other hand, while technological unemployment may be long-term, its problematicity might be short-term. If our AI future is genuinely as unpredictable and as revolutionary as I suspect, then even the sort of economic system we will have in that future is unknown.
A third problem is the threat of student dishonesty. During a conversation about GPT-3, a math professor told me “welcome to my world.” Mathematicians have long fought a losing battle against tools like Photomath, which allows students to snap a photo of their homework and then instantly solves it for them, showing all the needed steps. Now AI has come for the humanities and indeed for everyone. I have seen many university faculty insist that AI surely could not respond to their hyper-specific writing prompts, or assert that at best an AI could only write a barely passing paper, or appeal to this or that software that claims to spot AI products. Other researchers are trying to develop encrypted watermarks to identify AI output. All of this desperate optimism smacks of nothing more than the first stage of grief: denial.
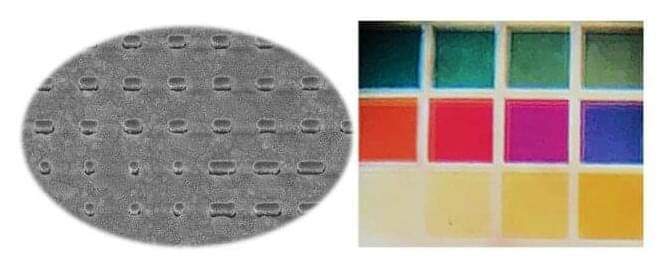
In a new approach to security that unites technology and art, EPFL researchers have combined silver nanostructures with polarized light to yield a range of brilliant colors, which can be used to encode messages.
Cryptography is something of a new field for Olivier Martin, who has been studying the optics of nanostructures for many years as head of the Nanophotonics and Metrology Lab EPFL’s School of Engineering. But after developing some new silver nanostructures in collaboration with the Center of MicroNanoTechnology, Martin and Ph.D. student Hsiang-Chu Wang noticed that these nanostructures reacted to polarized light in an unexpected way, which just happened to be perfect for encoding information.
They found that when polarized light was shone through the nanostructures from certain directions, a range of vivid and easily-identifiable colors was reflected back. These different colors could be assigned numbers, which could then be used to represent letters using the electronic communication standard code ASCII (American Standard Code for Information Interchange). To encode a secret message, the researchers applied a quaternary code using the digits 0, 1, 2 and 3 (as opposed to the more commonly used binary code 0 and 1). The result was a series of four-digit strings composed of different color combinations that could be used to spell out a message, and the method of chromo-encryption was born.

He is trying to influence the witness, alleged prosecutors.
Prosecutors of the FTX trial in the U.S. have asked the court to tighten the norms of the bail given to former CEO Sam Bankman-Fried (SBF) and bar him from using the encrypted messaging app Signal, The New York Times.
David Dee Delgado/Getty.
Although Bankman-Fried has pleaded not guilty to the charges levied against him, prosecutors state that he was well aware of the transactions that were taking place at the crypto exchange, which led to a sharp liquidity crunch and later its downfall. Billions of investor money have been lost and prosecutors claim that Bankman-Fried directed top brass at the company to hide liabilities worth $8 billion.

After years of delay under government pressure, Apple said Wednesday that it will offer fully encrypted backups of photos, chat histories and most other sensitive user data in its cloud storage system worldwide, putting them out of reach of most hackers, spies and law enforcement.
Maybe a New iPhone is a good idea for a second phone.
The one service Apple offered that could not be encrypted was iCloud. Now that will change.