When quantum computers become powerful enough, they could theoretically crack the encryption algorithms that keep us safe. The race is on to find new ones.



A phenomenon that often accompanies technological innovations involves how they tend to become smaller with their improvement over time. From televisions and communication devices like telephones to computers and microchip components, many of the technologies we use every day occupy a fraction of the space in our homes and offices that their predecessors did just decades ago.
In keeping with this trend, it is no surprise that a new tech developed by scientists at Sandia National Laboratories, in cooperation with the Max Planck Institute for the Science of Light, may soon replace cumbersome technologies than once required an entire room to operate, thanks to an ultrathin invention that could change the future of computation, encryption, and a host of other technologies.
At the heart of the invention and its function is a peculiar phenomenon that has perplexed physicists for decades, known as quantum entanglement.
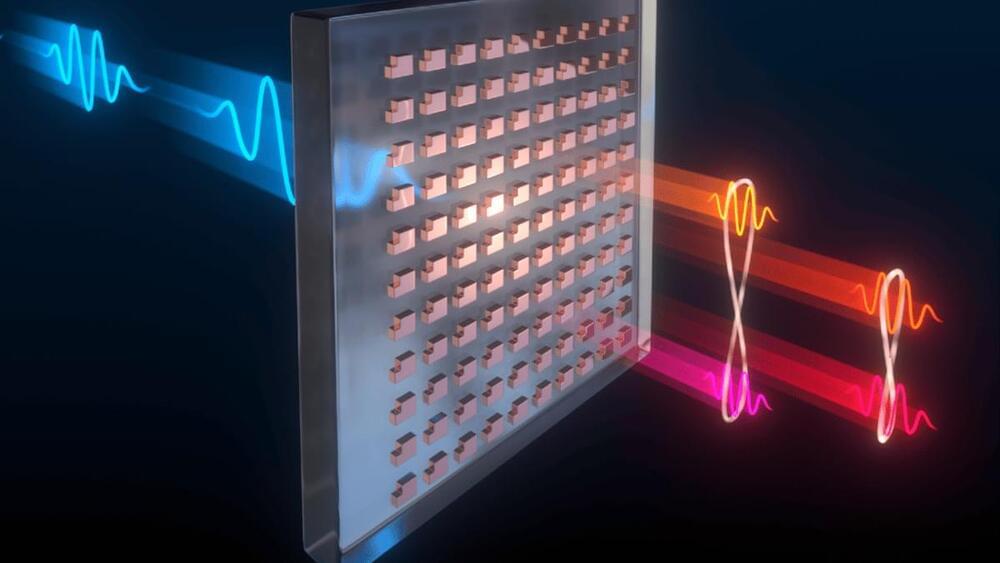
Scientists at Sandia National Laboratories and the Max Planck Institute have developed a way to produce a web of quantum entangled photons using a far more simple setup than usual. The key is a precisely patterned surface 100 times thinner than paper, which could replace a roomful of optical equipment.
Quantum entanglement is the bizarre-sounding phenomenon where two particles can become so entwined together that manipulating one will instantly affect its partner, no matter how far apart they may be. This forms the basis for emerging technologies like quantum computing and quantum encryption.
The problem is, generating entangled groups of photons can be tricky, and is usually done with large arrays of lasers, specialized crystals, and other optical equipment. But the Sandia and Max Planck team has a much simpler setup – a metasurface.

A growing number of ransomware groups are adopting a new tactic that helps them encrypt their victims’ systems faster while reducing the chances of being detected and stopped.
This tactic is called intermittent encryption, and it consists of encrypting only parts of the targeted files’ content, which would still render the data unrecoverable without using a valid decryptor+key.
For example, by skipping every other 16 bytes of a file, the encryption process takes almost half of the time required for full encryption but still locks the contents for good.

“So a quantum key distribution consists of two things: No. 1, got to have a quantum random number generator, and that’s one of the things that QNu Labs makes,” he said. “The second thing that you need is the receivers in which those two devices connect and be used to convey encrypted messages in this fashion.”
In military use, quantum key distribution would work best in point to point communication — that is, communicating from one person to another. Creating a “true network” that’s able to send the same encrypted message to multiple receivers at once is challenging because the encrypted bit that’s carrying the message eventually begins to lose its coherence and “drops away,” Herman said.
“In the military, where you’re sending extremely sensitive classified data from one office to the next, you want to make sure that no one’s going to be able to break into and decrypt that,” he said. “Well, [quantum key distribution] is definitely a way in which to carry that out.”

This post is also available in:  עברית (Hebrew)
עברית (Hebrew)
Bypassing complex encryption has become a main goal and pursuit to State-actors and cybercriminals alike. It has never been more important to focus on updated, resilient HTTPS configurations, according to the TLS Telemetry Report by F5 Labs, which uncovers the extent of internet encryption and the potential use or abuse of web encryption for malicious purposes.
Based on the screening of the top million websites in the world, the report claims that more than half of the web servers still allow unsecured RSA Exchange. In addition, the negation of authorization remains problematic, due to the prevalence of legacy servers updated only rarely.

An encryption tool co-created by a University of Cincinnati math professor will soon safeguard the telecommunications, online retail and banking and other digital systems we use every day.
The National Institute of Standards and Technology chose four new encryption tools designed to thwart the next generation of hackers or thieves. One of them, called CRYSTALS-Kyber, is co-created by UC College of Arts and Sciences math professor Jintai Ding.
“It’s not just for today but for tomorrow,” Ding said. “This is information that you don’t want people to know even 30 or 50 years from now.”

Although quantum computing is not commercially available, CISA (Cybersecurity and Infrastructure Security Agency) urges organizations to prepare for the dawn of this new age, which is expected to bring groundbreaking changes in cryptography, and how we protect our secrets.
The agency published a paper earlier in the week, calling for leaders to start preparing for the migration to stronger secret guarding systems, exploring risk mitigation methods, and participating in developing new standards.
Given the potential scope and capabilities of quantum technology, it is absolutely crucial not to repeat the mistakes made with AI—where regulatory failure has given the world algorithmic bias that hypercharges human prejudices, social media that favors conspiracy theories, and attacks on the institutions of democracy fueled by AI-generated fake news and social media posts. The dangers lie in the machine’s ability to make decisions autonomously, with flaws in the computer code resulting in unanticipated, often detrimental, outcomes. In 2021, the quantum community issued a call for action to urgently address these concerns. In addition, critical public and private intellectual property on quantum-enabling technologies must be protected from theft and abuse by the United States’ adversaries.
https://urldefense.com/v3/__https:/www.youtube.com/watch?v=5…MexaVnE%24
There are national defense issues involved as well. In security technology circles, the holy grail is what’s called a cryptanalytically relevant quantum computer —a system capable of breaking much of the public-key cryptography that digital systems around the world use, which would enable blockchain cracking, for example. That’s a very dangerous capability to have in the hands of an adversarial regime.
Experts warn that China appears to have a lead in various areas of quantum technology, such as quantum networks and quantum processors. Two of the world’s most powerful quantum computers were been built in China, and as far back as 2017, scientists at the University of Science and Technology of China in Hefei built the world’s first quantum communication network using advanced satellites. To be sure, these publicly disclosed projects are scientific machines to prove the concept, with relatively little bearing on the future viability of quantum computing. However, knowing that all governments are pursuing the technology simply to prevent an adversary from being first, these Chinese successes could well indicate an advantage over the United States and the rest of the West.
Over the past decade, digital cameras have been widely adopted in various aspects of our society, and are being massively used in mobile phones, security surveillance, autonomous vehicles, and facial recognition. Through these cameras, enormous amounts of image data are being generated, which raises growing concerns about privacy protection.
Some existing methods address these concerns by applying algorithms to conceal sensitive information from the acquired images, such as image blurring or encryption. However, such methods still risk exposure of sensitive data because the raw images are already captured before they undergo digital processing to hide or encrypt the sensitive information. Also, the computation of these algorithms requires additional power consumption. Other efforts were also made to seek solutions to this problem by using customized cameras to downgrade the image quality so that identifiable information can be concealed. However, these approaches sacrifice the overall image quality for all the objects of interest, which is undesired, and they are still vulnerable to adversarial attacks to retrieve the sensitive information that is recorded.
A new research paper published in eLight demonstrated a new paradigm to achieve privacy-preserving imaging by building a fundamentally new type of imager designed by AI. In their paper, UCLA researchers, led by Professor Aydogan Ozcan, presented a smart camera design that images only certain types of desired objects, while instantaneously erasing other types of objects from its images without requiring any digital processing.