A new hack called Hertzbleed can read snippets of data from computer chips remotely and could leave cryptography algorithms vulnerable to attack.



The Quantum ransomware, a strain first discovered in August 2021, were seen carrying out speedy attacks that escalate quickly, leaving defenders little time to react.
The threat actors are using the IcedID malware as one of their initial access vectors, which deploys Cobalt Strike for remote access and leads to data theft and encryption using Quantum Locker.
The technical details of a Quantum ransomware attack were analyzed by security researchers at The DFIR Report, who says the attack lasted only 3 hours and 44 minutes from initial infection to the completion of encrypting devices.
The 3D-printed containers keep a log of all break-in attempts, meaning your snail mail just got way safer.
Suppose you want to mail a court document to someone across the country—you don’t want anyone to see the secure information inside, of course. So, you seal it into a container that has special sensors built into its walls, and electronics that monitor the shield of sensors. Now, the container is armed and monitoring.
On the way to its intended recipient, let’s say the container is hacked. When the intended recipient later opens the container, they pull out the court document, along with an SD card (just like the ones you might use to store digital photos). They plug the card into a computer and look at the file. They see an encrypted historical record of the container’s experiences, from the time you put that document into the container and sealed it, up until the time they opened it. In the list of messages is a notification about a tampering attack, along with the date and time of the incident. The message also specifies the type of breach detected, such as the container being opened or cut.
A team at Los Alamos National Laboratory in New Mexico hopes this ability to see recorded, real-time security information about sensitive physical materials will become an everyday tool. Using a 3D printer, engineers built a prototype “Tamper-Evident Container” (TEC) that looks like a cylindrical box on the outside, but inside holds a complex network of sensors and electronics that record potential break-ins.
Researchers in Beijing have set a new quantum secure direct communication (QSDC) world record of 102.2 km (64 miles), smashing the previous mark of 18 km (11 miles), The Eurasian Times reported. Transmission speeds were extremely slow at 0.54 bits per second, but still good enough for text message and phone call encryption over a distance of 30 km (19 miles), wrote research lead Long Guilu in Nature. The work could eventually lead to hack-proof communication, as any eavesdropping attempt on a quantum line can be instantly detected.
QSDC uses the principal of entanglement to secure networks. Quantum physics dictates that entangled particles are linked, so that if you change the property of one by measuring it, the other will instantly change, too — effectively making hacking impossible. In theory, the particles stay linked even if they’re light-years apart, so such systems should work over great distances.
The same research team set the previous fiber record, and devised a “novel design of physical system with a new protocol” to achieve the longer distance. They simplified it by eliminating the “complicated active compensation subsystem” used in the previous model. “This enables an ultra-low quantum bit error rate (QBER) and the long-term stability against environmental noises.”

Scientists from Beijing set a new quantum secure direct communication (QSDC) world record of 102.2 km (64 miles), a massive leap over the previous record of 18 km (11 miles), according to The Eurasian Times.
The research could eventually lead to a massive quantum communications network that would be virtually hacker-proof due to the nature of the technology.
The researchers, who published their findings in a paper in Nature, demonstrated transmission speeds of 0.54 bits per second, much slower than communications using classical computing devices. Still, this was fast enough for phone call and text message encryption over a distance of 30 km (19 miles).

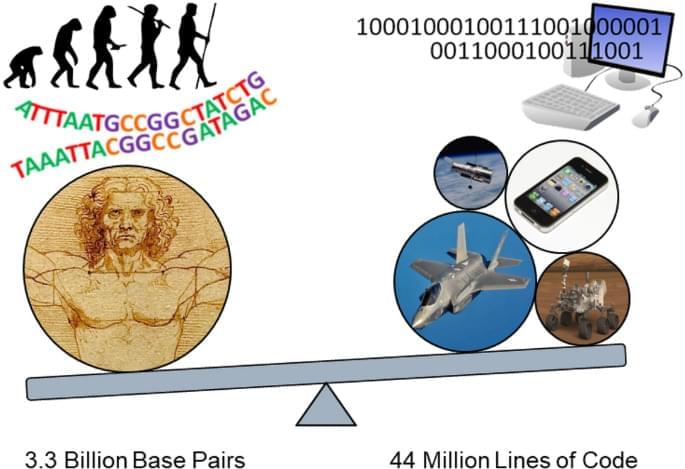
When knowledge has advanced to a state that includes a predictive understanding of the relationship between genome sequence and organism phenotype it will be possible for future engineers to design and produce synthetic organisms. However, the possibility of synthetic biology does not necessarily guarantee its feasibility, in much the same way that the possibility of a brute force attack fails to ensure the timely breaking of robust encryption. The size and range of natural genomes, from a few million base pairs for bacteria to over 100 billion base pairs for some plants, suggests it is necessary to evaluate the practical limits of designing genomes of similar complexity.

Homomorphic encryption is considered a next generation data security technology, but researchers have identified a vulnerability that allows them to steal data even as it is being encrypted.
“We weren’t able to crack homomorphic encryption using mathematical tools,” says Aydin Aysu, senior author of a paper on the work and an assistant professor of computer engineering at North Carolina State University. “Instead, we used side-channel attacks. Basically, by monitoring power consumption in a device that is encoding data for homomorphic encryption, we are able to read the data as it is being encrypted. This demonstrates that even next generation encryption technologies need protection against side-channel attacks.”
Homomorphic encryption is a way of encrypting data so that third parties cannot read it. However, homomorphic encryption still allows third parties and third-party technologies to conduct operations using the data. For example, a user could use homomorphic encryption to upload sensitive data to a cloud computing system in order to perform analyses of the data. Programs in the cloud could perform the analyses and send the resulting information back to the user, but those programs would never actually be able to read the sensitive data.
