A new report says it could take more than a decade to develop new cryptography schemes to keep data secure when quantum computers hit prime time.
Category: encryption – Page 53




Physicists race to demystify Einstein’s ‘spooky’ science
When it comes to fundamental physics, things can get spooky. At least that’s what Albert Einstein said when describing the phenomenon of quantum entanglement—the linkage of particles in such a way that measurements performed on one particle seem to affect the other, even when separated by great distances. “Spooky action at a distance” is how Einstein described what he couldn’t explain.
While quantum mechanics includes many mysterious phenomena like entanglement, it remains the best fundamental physical theory describing how matter and light behave at the smallest scales. Quantum theory has survived numerous experimental tests in the past century while enabling many advanced technologies: modern computers, digital cameras and the displays of TVs, laptops and smartphones. Quantum entanglement itself is also the key to several next-generation technologies in computing, encryption and telecommunications. Yet, there is no clear consensus on how to interpret what quantum theory says about the true nature of reality at the subatomic level, or to definitively explain how entanglement actually works.
According to Andrew Friedman, a research scientist at the University of California San Diego Center for Astrophysics and Space Sciences (CASS), “the race is on” around the globe to identify and experimentally close potential loopholes that could still allow alternative theories, distinct from quantum theory, to explain perplexing phenomena like quantum entanglement. Such loopholes could potentially allow future quantum encryption schemes to be hacked. So, Friedman and his fellow researchers conducted a “Cosmic Bell” test with polarization-entangled photons designed to further close the “freedom-of-choice” or “free will” loophole in tests of Bell’s inequality, a famous theoretical result derived by physicist John S. Bell in the 1960s. Published in the Aug. 20 issue of Physical Review Letters, their findings are consistent with quantum theory and push back to at least 7.

Government seeks Facebook help to wiretap Messenger — sources
SAN FRANCISCO (Reuters) — The U.S. government is trying to force Facebook Inc ( FB.O ) to break the encryption in its popular Messenger app so law enforcement may listen to a suspect’s voice conversations in a criminal probe, three people briefed on the case said, resurrecting the issue of whether companies can be compelled to alter their products to enable surveillance.
The previously unreported case in a federal court in California is proceeding under seal, so no filings are publicly available, but the three people told Reuters that Facebook is contesting the U.S. Department of Justice’s demand.
The judge in the Messenger case heard arguments on Tuesday on a government motion to hold Facebook in contempt of court for refusing to carry out the surveillance request, according to the sources, who spoke on condition of anonymity.

Futurists in Ethiopia are betting on artificial intelligence to drive development
“We should not start from steam and railways, or the old technologies—that is already done,” Assefa argues.
That makes sense to academics like Singh — though he also cautions that political forces are often slow to see the bigger picture. There is definitely an opportunity for developing countries, he says. “But any time we have a technological revolution, the political institutions have to catch up.”
A 2017 report (pdf) by the World Wide Web Foundation suggested that Ethiopian “intelligence services are using machine intelligence techniques to break encryption and find patterns in social media posts that can be used to identify dissidents.” And while mobile phone and internet penetration in Ethiopia is comparatively poor—a situation made worst amid widespread anti-government protests, which prompted an internet crackdown in February — the report added that government surveillance and oppression could increase as the use of smartphones expands.
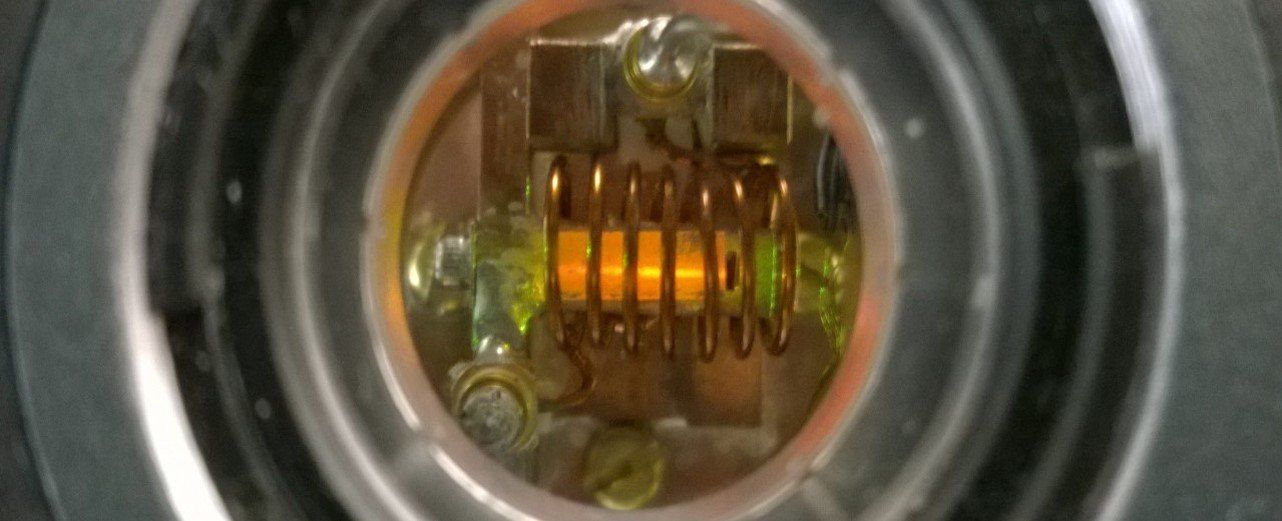
Ytterbium: The quantum memory of tomorrow
Quantum communication and cryptography are the future of high-security communication. But many challenges lie ahead before a worldwide quantum network can be set up, including propagating the quantum signal over long distances. One of the major challenges is to create memories with the capacity to store quantum information carried by light. Researchers at the University of Geneva (UNIGE), Switzerland, in partnership with CNRS, France, have discovered a new material in which an element, ytterbium, can store and protect the fragile quantum information even while operating at high frequencies. This makes ytterbium an ideal candidate for future quantum networks, where the aim is to propagate the signal over long distances by acting as repeaters. These results are published in the journal Nature Materials.
Quantum cryptography today uses optical fibre over several hundred kilometres and is marked by its high degree of security: it is impossible to copy or intercept information without making it disappear.
However, the fact that it is impossible to copy the signal also prevents scientists from amplifying it to diffuse it over long distances, as is the case with the Wi-Fi network.
How cryptography enables online shopping, cloud tech, and the blockchain
What do the Gallic Wars and online shopping have in common? The answer, believe it or not, is cryptography. Cryptography is the cement of the digital world, but it also has a long history that predates the digital era.
Most people do not realize that cryptography is a foundational element to our modern society. At it’s heart cryptography is about access to data, and controlling who can see and use it.
Don’t get your hopes up.