What’s next? Nanocavities in a diamond for small devices.
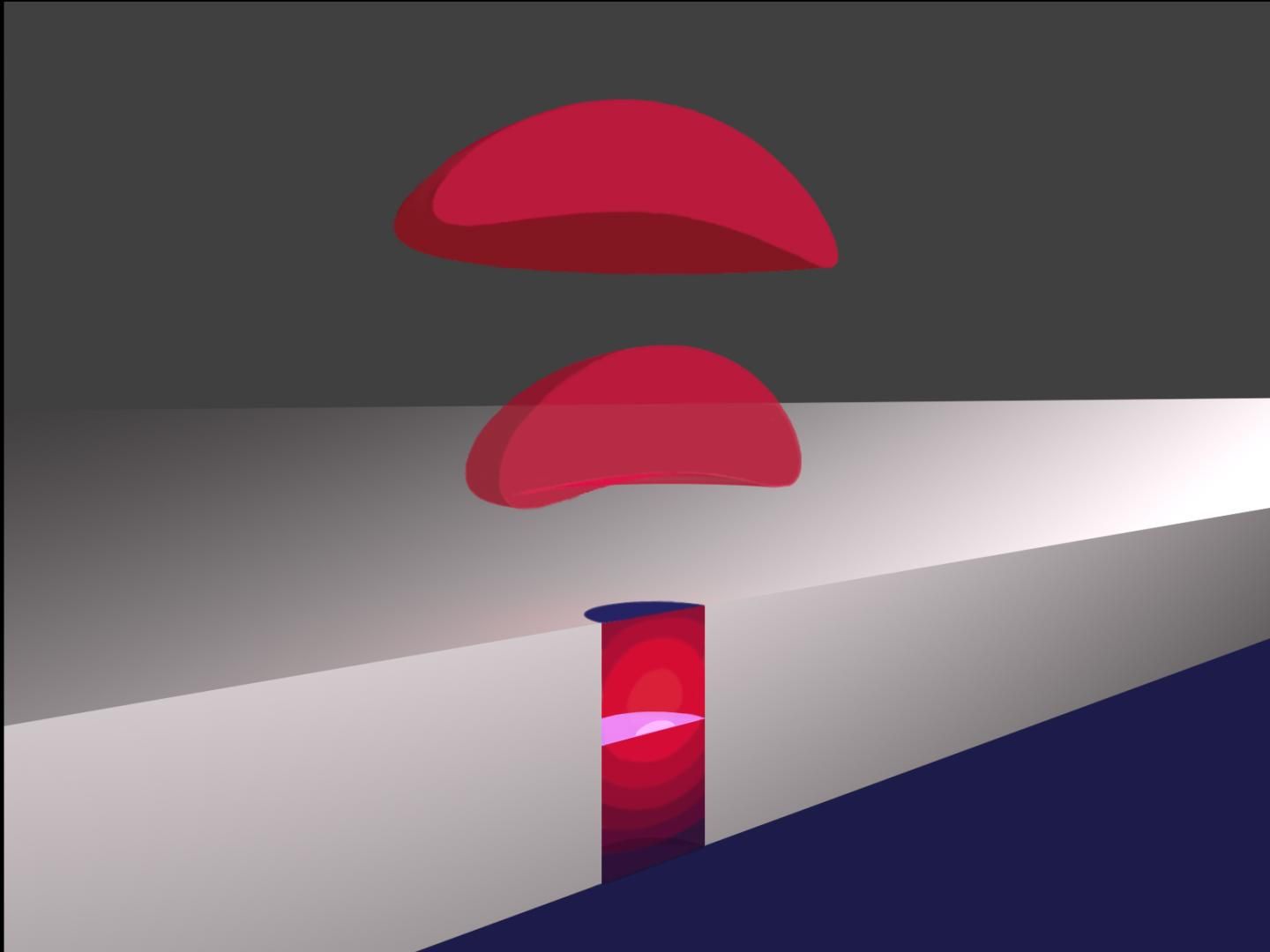
Researchers have developed a new type of light-enhancing optical cavity that is only 200 nanometers tall and 100 nanometers across. Their new nanoscale system represents a step toward brighter single-photon sources, which could help propel quantum-based encryption techniques under development.
Quantum encryption techniques, which are seen as likely to be central to future data encryption methods, use individual photons as an extremely secure way to encode data. A limitation of these techniques has been the ability to emit photons at high rates. “One of the most important figures of merit for single-photon sources is brightness — or collected photons per second — because the brighter it is, the more data you can transmit securely with quantum encryption,” said Yousif Kelaita of Stanford University.
In the journal Optical Materials Express, from The Optical Society (OSA), Kelaita and his colleagues show that their new nanocavity significantly increased the emission brightness of quantum dots — nanometer-scale semiconductor particles that can emit single photons.