Get Ready Folks! Imagine a QC DarkNet as it will too come.
Quantum teleportation brings to mind Star Trek’s transporter, where crew members are disassembled in one location to be reassembled in another. Real quantum teleportation is a much more subtle effect where information is transferred between entangled quantum states. It’s a quantum trick that could give us the ultimate in secure communication. While quantum teleportation experiments have been performed countless times in the lab, doing it in the real world has proved a bit more challenging. But a recent experiment using a dark fibre portion of the internet has brought quantum teleportation one step closer to real world applications.
The backbone of the internet is a network of optical fibre. Everything from your bank transactions to pictures of your cat travel as beams of light through this fibre network. However there is much more fibre that has been laid than is currently used. This unused portion of the network is known as dark fibre. Other than not being currently used, the dark fiber network has the same properties as the web we currently use. This new experiment used a bit of this dark web in Calgary to teleport a photon state under real world conditions.
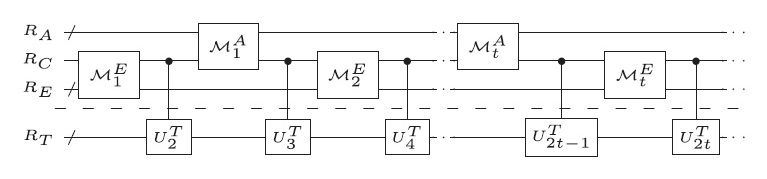
The basic process of quantum teleportation begins with two objects (in this case photons) that are quantumly entangled. This basically means the state of these two objects are connected in such a way that a measurement of one object affects the state of the other. For quantum teleportation, one of these entangled objects is measured in combination with the object to be “teleported” (another photon). The result of this measurement is then sent to the other location, where a similar combined measurement is made. Since the entangled objects are part of both measurements, quantum information can be “teleported.” This might seem like an awkward way to send information, but it makes for a great way to keep your messages secret. Using this method, Alice can basically encrypt a message using the entangled objects, send the encrypted message to Bob, who can then make his own measurement of the entangled state to decode the message.