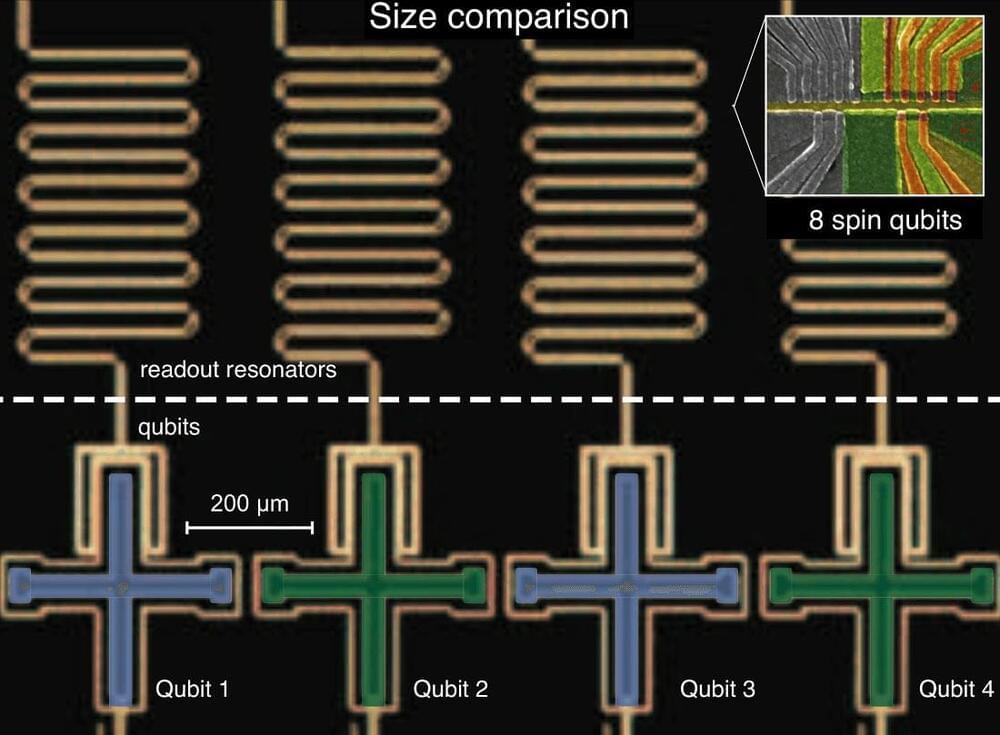
Quantum physicists at the University of Copenhagen are reporting an international achievement for Denmark in the field of quantum technology. By simultaneously operating multiple spin qubits on the same quantum chip, they surmounted a key obstacle on the road to the supercomputer of the future. The result bodes well for the use of semiconductor materials as a platform for solid-state quantum computers.
One of the engineering headaches in the global marathon towards a large functional quantum computer is the control of many basic memory devices – qubits – simultaneously. This is because the control of one qubit is typically negatively affected by simultaneous control pulses applied to another qubit. Now, a pair of young quantum physicists at the University of Copenhagen’s Niels Bohr Institute –PhD student, now Postdoc, Federico Fedele, 29 and Asst. Prof. Anasua Chatterjee, 32,– working in the group of Assoc. Prof. Ferdinand Kuemmeth, have managed to overcome this obstacle.
The brain of the quantum computer that scientists are attempting to build will consist of many arrays of qubits, similar to the bits on smartphone microchips. They will make up the machine’s memory.