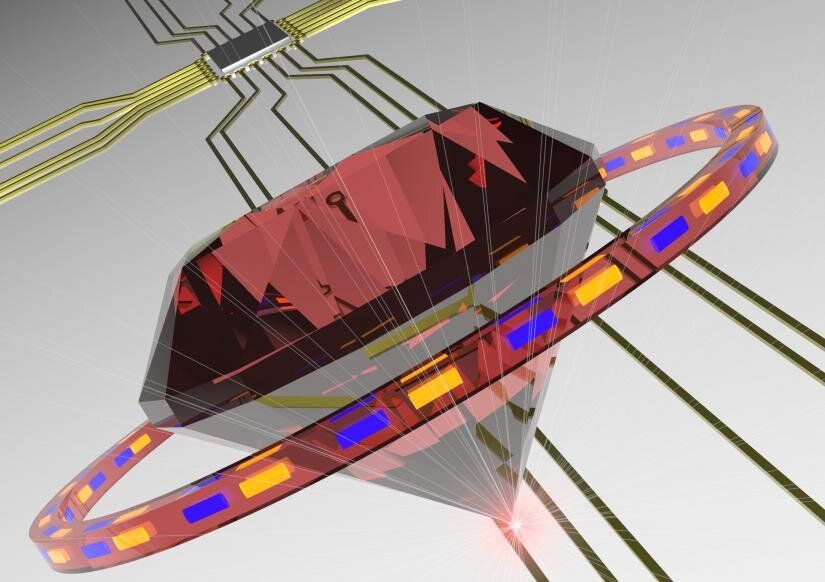
Marilyn Monroe famously sang that diamonds are a girl’s best friend, but they are also very popular with quantum scientists—with two new research breakthroughs poised to accelerate the development of synthetic diamond-based quantum technology, improve scalability, and dramatically reduce manufacturing costs.
While silicon is traditionally used for computer and mobile phone hardware, diamond has unique properties that make it particularly useful as a base for emerging quantum technologies such as quantum supercomputers, secure communications and sensors.
However there are two key problems; cost, and difficulty in fabricating the single crystal diamond layer, which is smaller than one millionth of a meter.