Lifeboat Editorial
Lydia Begag is a high school junior at Advanced Math and Science Academy in Massachusetts. She got our attention when she published an editorial critical of the school’s uniform policy. With eloquence and articulation, she laid out a brilliant and persuasive argument that the policy was anything but uniform. It was ambiguous, arbitrary and discriminatory.
I’m with Her
Ideas Regarding Sex Equality
—Forget the Rest
Political and social turmoil are everywhere we turn, especially in the early months of 2017. Lunch conversations, small talk at work, and, of course, the media we consume have all become related to a singular topic: the United States government and its workings. Emotionally, I want to curl up in a ball and block out the political nonsense being spewed left and right until the day I die (pun very much intended)—but I feel intellectually obliged to confront the controversy.
All who live and breath America understand why politics have always been a hot topic for debate. Every ideology, action, and word are potentially contentious. Such is especially the case with modern feminism. Everyone seems to have a different opinion of it and portrays it in different ways, from the group of men wolf whistling at a woman on her way to her car after work to powerful cultural figures who associate themselves with the movement. Before we can even begin to familiarize ourselves with conflicting beliefs towards women and feminism in general and their reflection of a worrisome mentality, it is crucial to first understand feminism’s roots in the United States, and how interpretations of the word and the movement have varied throughout the years.

Feminism begins its legacy in 19th-century America, where its first-wave arises at the Seneca Falls Convention of July 1948. Prominent feminists of the era (including Elizabeth Cady Stanton—more on her later!) issued a Declaration of Sentiments for women that emulated the Declaration of Independence their husbands had crafted 170 years earlier. The document asserted that women had fundamental rights that were denied without cause, including suffrage. However, the first-wave feminist movement raised a series of questions regarding whether it was acceptable to promote black civil rights over and into women’s rights. Should the rights of black men be prioritized over establishing and recognizing rights for women? Should black women be considered in the fight for gender equality as well, or would that undermine the cause white women had been fighting for for so long? The moral conflict eventually resulted in a success for the women’s suffrage movement in 1920. White women, led by famous feminists such as Stanton, Alice Paul, and Lucy Burns, gained the right to vote in federal and state elections via the 19th Amendment to the U.S. Constitution. Women of color, however, were left in the dust and did not start to gain suffrage until 1965. This type of exclusive feminism did not end when women of color gained suffrage; it has proven itself to be significant even today.
The list of American feminist milestones goes on and on. Women experienced sexual liberation in the Roaring 20s, when life was grander and more exquisite than ever. They essentially took over maintenance of the U.S. economy when men went to fight in the world wars, and Rosie the Riveter was born.  Women were also becoming increasingly influential in politics. Such milestones included the first woman to run for president on a major-party ticket in 1972 to landmark Supreme Court cases asserting that a right to privacy does include guaranteed legal accessibility to abortion and contraceptives. Title 9, the amendment to the Education Amendments Act of 1972, enabled girls in schools across the country to receive the same benefits as their male peers. All of these milestones reshaped a woman’s role in society throughout the 20th century onwards, but they did not come without drawbacks. The ’20s was an intense era of sexist and classist attitudes. Female sexual liberation resulted in extreme objectification. After WWI was over and soldiers came home, women were whisked back into the households to resume their roles as obedient housewives. Male dominance made running for public office harder for a woman, despite having the opportunity. And let us not forget the controversy surrounding a woman’s right to privacy. A significant factor involves religious morals and/or other ethical reasoning that are not related to gender equality, but it is impossible to ignore the misogynistic rationale that many pro-lifers exhibit. All of the achievements we’ve had have seemingly been countered by just as much dissent as support, a persistent reality since Abigail Adams urged her husband to support gender equality.
Women were also becoming increasingly influential in politics. Such milestones included the first woman to run for president on a major-party ticket in 1972 to landmark Supreme Court cases asserting that a right to privacy does include guaranteed legal accessibility to abortion and contraceptives. Title 9, the amendment to the Education Amendments Act of 1972, enabled girls in schools across the country to receive the same benefits as their male peers. All of these milestones reshaped a woman’s role in society throughout the 20th century onwards, but they did not come without drawbacks. The ’20s was an intense era of sexist and classist attitudes. Female sexual liberation resulted in extreme objectification. After WWI was over and soldiers came home, women were whisked back into the households to resume their roles as obedient housewives. Male dominance made running for public office harder for a woman, despite having the opportunity. And let us not forget the controversy surrounding a woman’s right to privacy. A significant factor involves religious morals and/or other ethical reasoning that are not related to gender equality, but it is impossible to ignore the misogynistic rationale that many pro-lifers exhibit. All of the achievements we’ve had have seemingly been countered by just as much dissent as support, a persistent reality since Abigail Adams urged her husband to support gender equality.
We are currently in the era of what fundamentalist feminists call “Take A Shot Every time You Offend Someone With One of Your Comments.” That term, of course, is colloquialism at its finest. You’re probably more familiar with something called third-wave feminism. This type of feminism has become increasingly less focused on the kind of feminism Stanton was prominent for (Yay! Exclusivity!) and more on queer and non-white women. The concept of intersectionality was introduced in the late ’80s just before this third wave began. It has received great support by women of color and those who had always been ignored by exclusive feminists, but as we already know, dissent is just around the corner.
The most popular criticism focuses on a lack of cohesion. First wave feminism fought for and gained female suffrage. The second wave fought for the right for women to have access to equal opportunity in the workforce and an end to legal sex discrimination. What is third  wave feminism’s goal? Is there even a goal, or are its advocates serving as the world’s determinators of what is PC and what is not? The stigma around the feminist movement has existed ever since its origins in this country, but the increasing disassociation of women from the term ‘feminism’ has become alarming in recent years. For every outspoken celebrity and political feminist there is out there (think Emma Watson, Shonda Rhimes, Nancy Pelosi) there is an equally prominent female figure that opposes the movement, such as Lana del Rey, Tomi Lahren, and Shailene Woodley. Here’s the kicker: these role models usually aren’t misogynistic or demeaning. They simply seek to avoid affiliation with the word itself and its modern day supporters. This is understandable; we’re a country founded on grounds of freedom. If a person doesn’t want to associate themselves with a movement, there’s no obligation to. However, the fact that women don’t even want to be labeled feminists because of what it has come to signify is something I find very problematic. I don’t see this as an inadequate reflection of what 21st century women believe in, but rather a poor reflection on the feminist crusade. The way I look at it is this: apples don’t fall off a tree because they are too heavy. Rather, they fall off because the stem is too weak to support them.
wave feminism’s goal? Is there even a goal, or are its advocates serving as the world’s determinators of what is PC and what is not? The stigma around the feminist movement has existed ever since its origins in this country, but the increasing disassociation of women from the term ‘feminism’ has become alarming in recent years. For every outspoken celebrity and political feminist there is out there (think Emma Watson, Shonda Rhimes, Nancy Pelosi) there is an equally prominent female figure that opposes the movement, such as Lana del Rey, Tomi Lahren, and Shailene Woodley. Here’s the kicker: these role models usually aren’t misogynistic or demeaning. They simply seek to avoid affiliation with the word itself and its modern day supporters. This is understandable; we’re a country founded on grounds of freedom. If a person doesn’t want to associate themselves with a movement, there’s no obligation to. However, the fact that women don’t even want to be labeled feminists because of what it has come to signify is something I find very problematic. I don’t see this as an inadequate reflection of what 21st century women believe in, but rather a poor reflection on the feminist crusade. The way I look at it is this: apples don’t fall off a tree because they are too heavy. Rather, they fall off because the stem is too weak to support them.
This creation of a conflict within a conflict has led to major confusion on what “right” feminism is. As defined by Merriam Webster, “feminism” is the theory of the political, economic, and social equality of the sexes. This most basic meaning of the word is something most women, if not all, should consider when they debate whether or not to label themselves a feminist. Sex equality is really the only thing the third-wave feminist movement should be focused on. Issues such as racial inequality, and rights for LGBT and disabled persons, are a matter for a cause much broader than feminism (think egalitarianism). The more narrow a movement and its fight becomes, the more likely it is to accomplish its goals. The first two waves of feminism all had a set goal in mind, which was something that followed core feminism to the nines. In the midst of all of the social unrest that has risen since the ’80s, the feminist movement has been trying to take over the egalitarianist one. However, if women ever wish to gain social equality between the sexes, it is necessary to narrow the cause to its fundamental roots.
Another issue with the modern feminist movement is that, in the effort towards sex equality, many feminists have interpreted being equal to men as trying to act just like them. Men and women are different, biologically and perhaps psychologically, but of equal value. To quote Mary Ramirez’s  “Dear Daughter: Here’s Why I Didn’t March For You”: “…we are biologically and physically and emotionally different from men, but that doesn’t mean we’re less. It means we’re special.”
“Dear Daughter: Here’s Why I Didn’t March For You”: “…we are biologically and physically and emotionally different from men, but that doesn’t mean we’re less. It means we’re special.”
Nonetheless, achieving social equality between the sexes is something I consider crucial, particularly for the girls just starting to grow up in this country. It is disheartening for women to live in a world where, from the moment we start to grow up and find ourselves in a male-centric society, life becomes a tale of denigration and overt sexualization. However, the problem with using modern feminism to change this sexist attitude is that it has turned into a male resentment club, and no longer seems to revolve around sex equality in society. Off the top of my head, I can think of multiple times where the “feminists” surrounding me on a daily basis have remarked on female superiority or denounced women who do not wholeheartedly accept their idea of feminism. Feminism should preach equality and acceptance. Instead, it has turned into a catty game of doing to the men what the men have done to us. 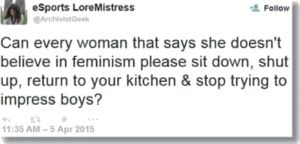 We live in a world where raising people up has turned into knocking others down. Vulgarity and impertinence has turned into the ideal image of a “strong” woman, and has become more and more acceptable. The idea of a feminist who respects others’ opinions has seemingly been swapped with one that thrives off of the idea of being regarded as “bitchy,” angry, or disrespectful. We’ve come a long way since our feminist founding mothers marched down Pennsylvania Avenue fighting for suffrage, and unfortunately, it’s not for the best.
We live in a world where raising people up has turned into knocking others down. Vulgarity and impertinence has turned into the ideal image of a “strong” woman, and has become more and more acceptable. The idea of a feminist who respects others’ opinions has seemingly been swapped with one that thrives off of the idea of being regarded as “bitchy,” angry, or disrespectful. We’ve come a long way since our feminist founding mothers marched down Pennsylvania Avenue fighting for suffrage, and unfortunately, it’s not for the best.
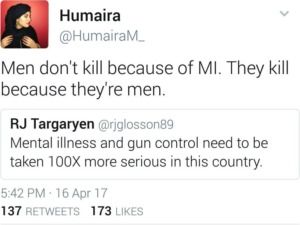 Envisioning myself in the world of politics five or ten years down the road…I won’t pretend it doesn’t worry me at times.Influential female politicians over the years have found not their beliefs or their policy agendas as the primary subject of media conversation, but rather whether or not they’re menstruating or have considered cosmetic surgery. Seeing myself and others in my current situation has worried me as well. Despite growing up in a privileged setting where I receive nothing but acceptance from my family, the school and work environment has offered me and similar girls slut-shaming, catcalling, and the craftiest of off-hand remarks (“Who are you trying to impress today with that outfit?”). A multitude of women who come from different backgrounds have experienced similar toxicity in their surroundings. Ultimately, any setting for a woman can be a problematic one, and a promotion of classic feminism could turn things around. To me, an advocacy for respect on both sexes’ parts—rather than claimed superiority—would be transformative in making these conditions for bearable for young American women and men. Right now, what we have is extreme exclusivity and not enough acceptance.
Envisioning myself in the world of politics five or ten years down the road…I won’t pretend it doesn’t worry me at times.Influential female politicians over the years have found not their beliefs or their policy agendas as the primary subject of media conversation, but rather whether or not they’re menstruating or have considered cosmetic surgery. Seeing myself and others in my current situation has worried me as well. Despite growing up in a privileged setting where I receive nothing but acceptance from my family, the school and work environment has offered me and similar girls slut-shaming, catcalling, and the craftiest of off-hand remarks (“Who are you trying to impress today with that outfit?”). A multitude of women who come from different backgrounds have experienced similar toxicity in their surroundings. Ultimately, any setting for a woman can be a problematic one, and a promotion of classic feminism could turn things around. To me, an advocacy for respect on both sexes’ parts—rather than claimed superiority—would be transformative in making these conditions for bearable for young American women and men. Right now, what we have is extreme exclusivity and not enough acceptance.
Want to call yourself a feminist? Great! Reluctant to associate yourself with the movement but still support sex equality? Sounds good! Don’t support sex equality and a reversal of traditional gender roles? That is still okay! Obviously if an opinion undermines the cause you are fighting for, you’re not inclined to encourage it. But what the American public needs to realize is that, when advocates contradict the cause of unity and respect with their actions and words change will not come. Crudity does not empower you; it only cheapens you.
As mentioned before, narrowing down the movement’s goals is also crucial in moving forward. In comparison to many nations around the world, the United States has seen great success when it comes to fighting for sex equality. The third-wave feminist movement does have some valid issues to advocate for—domestic violence, raising awareness for rape victims, pay discrimination, etc.—but also chooses to focus on trivial causes like Free the Nipple and eliminating “manspreading.” Perhaps it is because we have obtained legal equality (thanks, first two waves!). But now that social equity has become the main focus, a blur of ideas and beliefs have resulted in a chaotic, incohesive movement. If you consider feminism at its core, the social issue to fight for is clear. There are many causes worth fighting for: racial inequality, ableism, and marriage justness, to name a few. But for the love of God, leave the aspects that do not relate to sex equality for the egalitarians. They’re there for a reason.
Author’s Note: This is my first article for Lifeboat Foundation.
Add comments below. I will drop in from time to time to respond.
— Lydia Begag








 Women were also becoming increasingly influential in politics. Such milestones included the first woman to run for president on a major-party ticket in 1972 to landmark Supreme Court cases asserting that a right to privacy does include guaranteed legal accessibility to abortion and contraceptives. Title 9, the amendment to the Education Amendments Act of 1972, enabled girls in schools across the country to receive the same benefits as their male peers. All of these milestones reshaped a woman’s role in society throughout the 20th century onwards, but they did not come without drawbacks. The ’20s was an intense era of sexist and classist attitudes. Female sexual liberation resulted in extreme objectification. After WWI was over and soldiers came home, women were whisked back into the households to resume their roles as obedient housewives. Male dominance made running for public office harder for a woman, despite having the opportunity. And let us not forget the controversy surrounding a woman’s right to privacy. A significant factor involves religious morals and/or other ethical reasoning that are not related to gender equality, but it is impossible to ignore the misogynistic rationale that many pro-lifers exhibit. All of the achievements we’ve had have seemingly been countered by just as much dissent as support, a persistent reality since Abigail Adams urged her husband to support gender equality.
Women were also becoming increasingly influential in politics. Such milestones included the first woman to run for president on a major-party ticket in 1972 to landmark Supreme Court cases asserting that a right to privacy does include guaranteed legal accessibility to abortion and contraceptives. Title 9, the amendment to the Education Amendments Act of 1972, enabled girls in schools across the country to receive the same benefits as their male peers. All of these milestones reshaped a woman’s role in society throughout the 20th century onwards, but they did not come without drawbacks. The ’20s was an intense era of sexist and classist attitudes. Female sexual liberation resulted in extreme objectification. After WWI was over and soldiers came home, women were whisked back into the households to resume their roles as obedient housewives. Male dominance made running for public office harder for a woman, despite having the opportunity. And let us not forget the controversy surrounding a woman’s right to privacy. A significant factor involves religious morals and/or other ethical reasoning that are not related to gender equality, but it is impossible to ignore the misogynistic rationale that many pro-lifers exhibit. All of the achievements we’ve had have seemingly been countered by just as much dissent as support, a persistent reality since Abigail Adams urged her husband to support gender equality. wave feminism’s goal? Is there even a goal, or are its advocates serving as the world’s determinators of what is PC
wave feminism’s goal? Is there even a goal, or are its advocates serving as the world’s determinators of what is PC  “Dear Daughter: Here’s Why I Didn’t March For You”: “…we are biologically and physically and emotionally different from men, but that doesn’t mean we’re less. It means we’re special.”
“Dear Daughter: Here’s Why I Didn’t March For You”: “…we are biologically and physically and emotionally different from men, but that doesn’t mean we’re less. It means we’re special.” We live in a world where raising people up has turned into knocking others down. Vulgarity and impertinence has turned into the ideal image of a “strong” woman, and has become more and more acceptable. The idea of a feminist who respects others’ opinions has seemingly been swapped with one that thrives off of the idea of being regarded as “bitchy,” angry, or disrespectful. We’ve come a long way since our feminist founding mothers marched down Pennsylvania Avenue fighting for suffrage, and unfortunately, it’s not for the best.
We live in a world where raising people up has turned into knocking others down. Vulgarity and impertinence has turned into the ideal image of a “strong” woman, and has become more and more acceptable. The idea of a feminist who respects others’ opinions has seemingly been swapped with one that thrives off of the idea of being regarded as “bitchy,” angry, or disrespectful. We’ve come a long way since our feminist founding mothers marched down Pennsylvania Avenue fighting for suffrage, and unfortunately, it’s not for the best. Envisioning myself in the world of politics five or ten years down the road…I won’t pretend it doesn’t worry me at times.Influential female politicians over the years have found
Envisioning myself in the world of politics five or ten years down the road…I won’t pretend it doesn’t worry me at times.Influential female politicians over the years have found 
