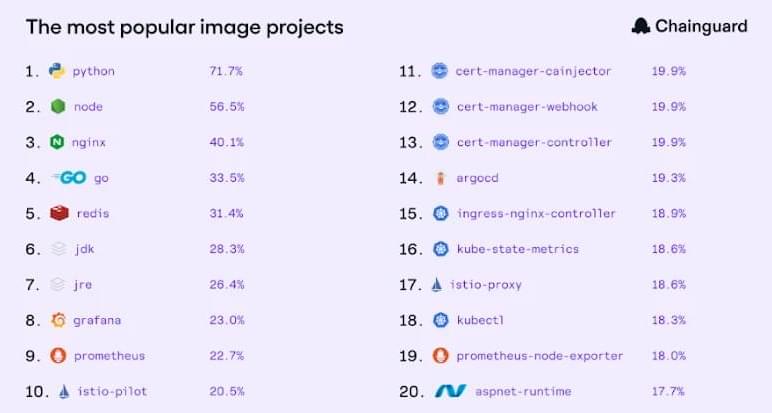
President Donald Trump decided to let Nvidia Corp. sell its H200 artificial intelligence chips to China after concluding the move carried a lower security risk because the company’s Chinese archrival, Huawei Technologies Co., already offers AI systems with comparable performance, according to a person familiar with the deliberations.
Administration officials who weighed whether to clear Nvidia’s H200 had considered multiple possible scenarios, factoring in the views of national security hawks in Washington, said the person. Options ranged from exporting zero AI chips to China to allowing exports of everything to flood the Chinese market and overwhelm Huawei. Ultimately the policy backed by Trump called for clearing H200s to China while holding back the latest Nvidia chips for American customers, the person said.