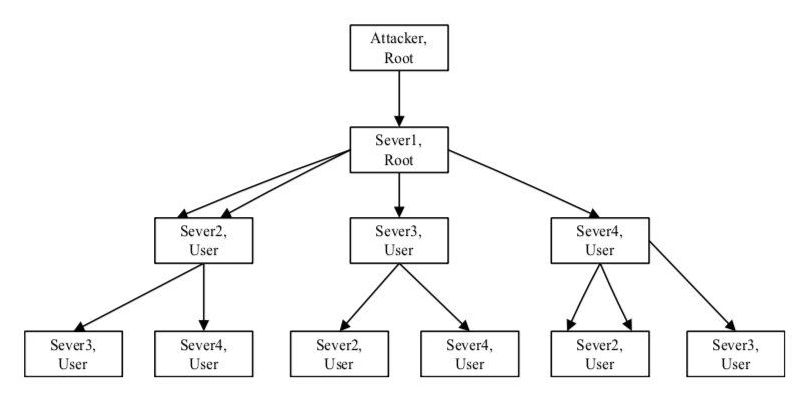
A growing number of devices are now connected to the internet and are capable of collecting, sending and receiving data. This interconnection between devices, referred to as the Internet of Things (IoT), poses serious security threats, as cyberattackers can now target computers and smartphones, but also a vast array of other devices, such as tablets, smart watches, smart home systems, transportation systems and so on.
For the time being, examples of large-scale IoT implementations (e.g. connected infrastructure, cities, etc.) are somewhat limited, yet they could soon become widespread, posing significant risks for businesses and public services that heavily rely on the internet in their daily operations. To mitigate these risks, researchers have been trying to develop security measures to protect devices connected to the internet from wireless network attacks.
To this end, two researchers at Baoji University of Arts and Sciences, in China, have recently developed a new method to defend devices in an IOT environment from wireless network attacks. Their approach, presented in a paper published in Springer’s International Journal of Wireless Information Networks, combines a deep neural network with a model based on game theory, a branch of mathematics that proposes strategies for dealing with situations that entail competition between different parties.
Read more