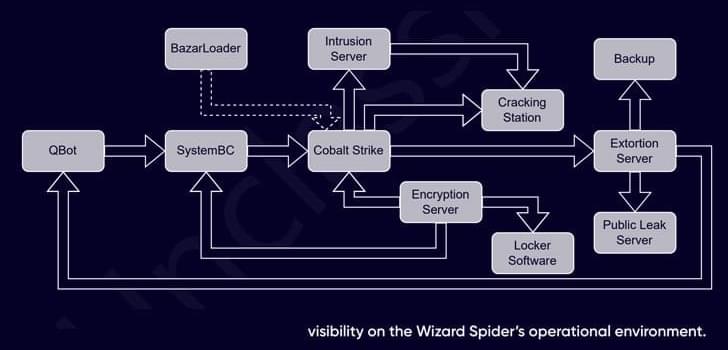
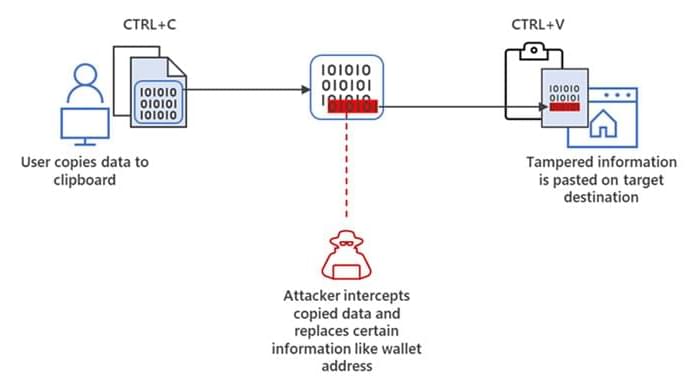
Trend Micro says it patched a DLL hijacking flaw in Trend Micro Security used by a Chinese threat group to side-load malicious DLLs and deploy malware.
As Sentinel Labs revealed in an early-May report, the attackers exploited the fact that security products run with high privileges on Windows to plant and load their own maliciously crafted DLL into memory, allowing them to elevate privileges and execute code.
“Trend Micro is aware of some research that was published on May 2, 2022, regarding a purported Central-Asian-based threat actor dubbed ‘Moshen Dragon’ that had deployed malware clusters that attempted to hijack various popular security products, including one from Trend Micro,” the cybersecurity company said.