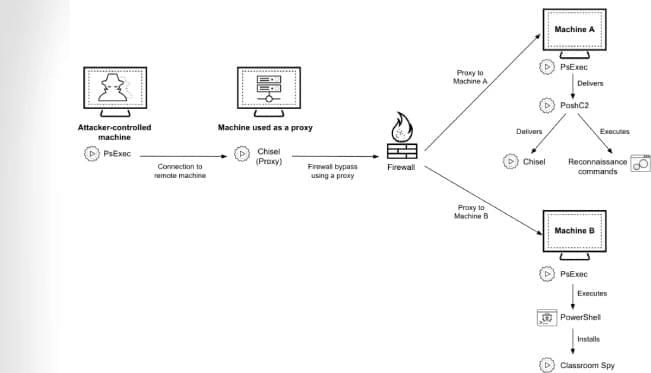
Cybersecurity researchers have flagged the tactical similarities between the threat actors behind the RomCom RAT and a cluster that has been observed delivering a loader dubbed TransferLoader.
Enterprise security firm Proofpoint is tracking the activity associated with TransferLoader to a group dubbed UNK_GreenSec and the RomCom RAT actors under the moniker TA829. The latter is also known by the names CIGAR, Nebulous Mantis, Storm-0978, Tropical Scorpius, UAC-0180, UAT-5647, UNC2596, and Void Rabisu.
The company said it discovered UNK_GreenSec as part of its investigation into TA829, describing it as using an “unusual amount of similar infrastructure, delivery tactics, landing pages, and email lure themes.”