Threat actors exploit ESXi systems as C2 tunnels, leveraging SSH for stealthy persistence, Sygnia reports.



Microsoft has started testing a new “scareware blocker” feature for the Edge web browser on Windows PCs, which uses machine learning (ML) to detect tech support scams.
Scareware scams (also known as tech support scams) have been a pervasive threat for years. The scammers use aggressive landing pages to persuade potential victims that their devices have been compromised with malware and then try to gain remote access to targets’ systems by pressuring them to call a fake tech support number.
Defender SmartScreen, which also protects Edge users from scams, activates after an abusive site is detected and added to its index of malicious web pages to safeguard users globally within minutes.

Today we’re announcing ChatGPT Gov, a new tailored version of ChatGPT designed to provide U.S. government agencies with an additional way to access OpenAI’s frontier models.
Agencies can deploy ChatGPT Gov in their own Microsoft Azure commercial cloud or Azure Government cloud on top of Microsoft’s Azure’s OpenAI (opens in a new window) Service. Self-hosting ChatGPT Gov enables agencies to more easily manage their own security, privacy, and compliance requirements, such as stringent cybersecurity frameworks (IL5, CJIS, ITAR, FedRAMP High). Additionally, we believe this infrastructure will expedite internal authorization of OpenAI’s tools for the handling of non-public sensitive data. Use of ChatGPT Gov is subject to our usage policies, like other OpenAI services.

The world of quantum physics is experiencing a second revolution, which will drive an exponential leap in the progress of computing, the internet, telecommunications, cybersecurity and biomedicine.
Quantum technologies are attracting more and more students who want to learn about concepts from the subatomic world—such as quantum entanglement or quantum superposition —to explore the innovative potential of quantum science.
In fact, understanding the non-intuitive nature of quantum technology concepts and recognizing their relevance to technological progress is one of the challenges of 2025, declared the International Year of Quantum Science and Technology by UNESCO.
Find out more about Bitdefender’s two decades of unparalleled cybersecurity excellence: https://bitdefend.me/StarTalkTA
Could we create warp drive someday? In this Star Trek-themed episode, Neil deGrasse Tyson and co-host Chuck Nice team up with astrophysicist Charles Liu to dive into the science, technology, and legacy of one of the most influential sci-fi franchises of all time: Star Trek.
We answer questions about quantum entanglement, the size of electrons, and the real science behind Trek tech or Treknology. How close are we to warp drives, transporters, and subspace communication? You might be surprised to hear what’s theoretically possible and what remains in the realm of science fiction.
We discuss technology that exists already and the solutions to storytelling challenges through warp drives and dilithium crystals. Learn about the show’s physics, from phasers and antimatter to the mycelium network’s fascinating parallels with fungal biology. How do you store antimatter without it annihilating? Plus, find out who everyone’s favorite characters are and who they relate to most.
As we reflect on the series’ 23rd-century vision, we ask: Could humanity achieve Trek-level tech by 2260? We discuss the physics we’re missing and the collective imagination and determination it takes to advance our understanding of the universe.
Get ‘The Handy Quantum Physics Answer Book’: https://amzn.to/4frhizV
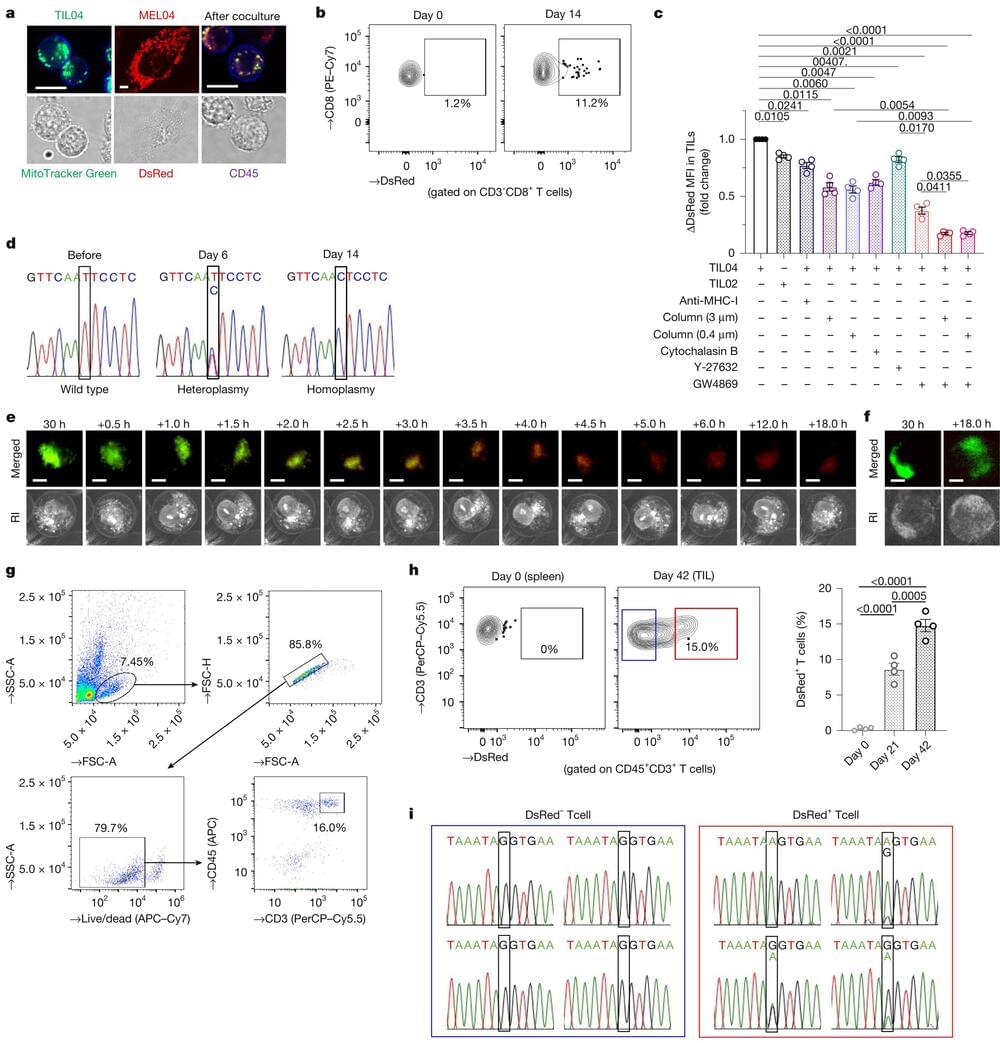
Research led by the Chiba Cancer Center Research Institute in Japan has discovered a surprising way cancer evades the immune system. It essentially hacks the immune cells, transferring its own faulty mitochondrial DNA (mtDNA) into the T-cells meant to attack it.
This sneaky move weakens the immune cells, making them less effective at stopping the tumor. The findings could help explain why some cancer treatments, like immunotherapy, are effective for some patients but not others.
In the study, “Immune evasion through mitochondrial transfer in the tumor microenvironment,” published in Nature, the multi-group collaboration looked at how cancer cells interact with tumor-infiltrating lymphocytes, a type of T-cell that typically fights tumors. The research is also featured in a News and Views piece.
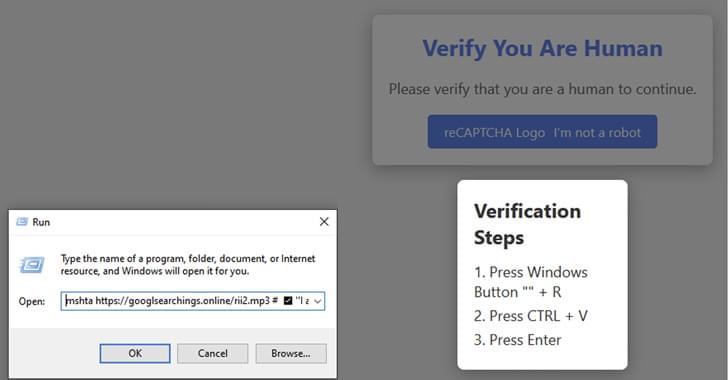
Cybersecurity researchers are calling attention to a new malware campaign that leverages fake CAPTCHA verification checks to deliver the infamous Lumma information stealer.
“The campaign is global, with Netskope Threat Labs tracking victims targeted in Argentina, Colombia, the United States, the Philippines, and other countries around the world,” Leandro Fróes, senior threat research engineer at Netskope Threat Labs, said in a report shared with The Hacker News.
“The campaign also spans multiple industries, including healthcare, banking, and marketing, with the telecom industry having the highest number of organizations targeted.”

Hackers are distributing close to 1,000 web pages mimicking Reddit and the WeTransfer file sharing service that lead to downloading the Lumma Stealer malware.
On the fake pages, the threat actor is abusing the Reddit brand by showing a fake discussion thread on a specific topic. The thread creator asks for help to download a specific tool, another user offers to help by uploading it to WeTransfer and sharing the link, and a third thanks him to make everything appear legitimate.
Unsuspecting victims clicking on the link are taken to a fake WeTransfer site that mimicks the interface of the popular file-sharing service. The ‘Download’ button leads to the Lumma Stealer payload hosted on “weighcobbweo[.]top.”

