Deals get remote islanders online, but fears linger over stranded investment, data security.
SHAUN TURTON and RURIKA IMAHASHI.

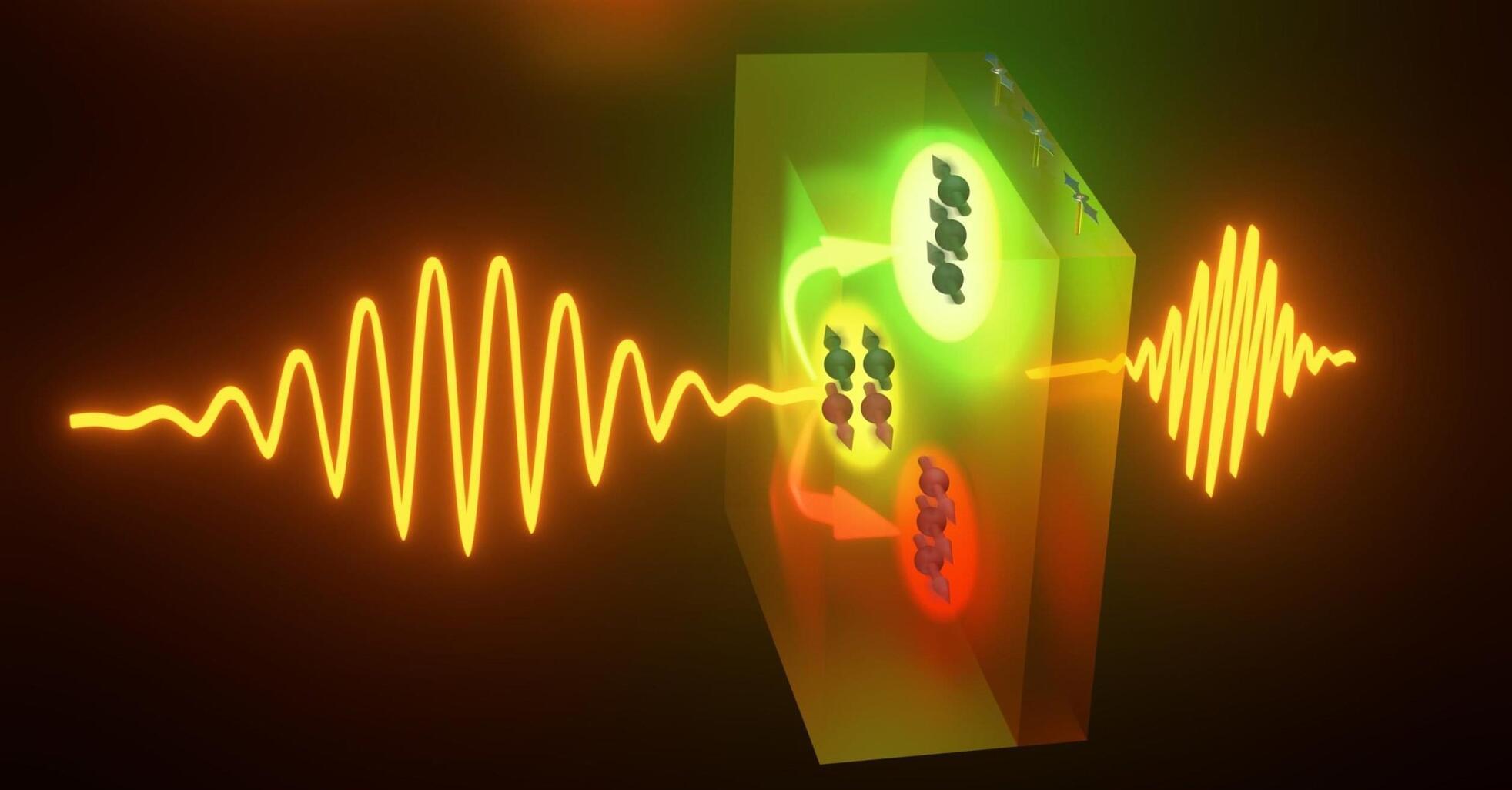
Quantum entanglement, one of the strangest and most powerful aspects of physics, has just been taken to a new level with the use of metasurfaces.
Researchers have discovered a way to create quantum holograms, where entangled photons encode intricate information with unprecedented precision. By leveraging the properties of metasurfaces, they demonstrated control over entangled holographic letters, opening doors to secure quantum communication and even anti-counterfeiting technology.
Unlocking the mysteries of quantum entanglement.

In today’s AI news, OpenAI and Google are pushing the US government to allow their AI models to train on copyrighted material. Both companies outlined their stances in proposals published this week, with OpenAI arguing that applying fair use protections to AI “is a matter of national security.” The proposals come in response to a request from the White House, which asked for input on Trump’s AI Action Plan.
In other advancements, one of the bigger players in automation has scooped up a startup in the space in hopes of taking a bigger piece of that market. UiPath, as part of a quarterly result report last night that spelled tougher times ahead, also delivered what it hopes might prove a silver lining. It said it had acquired, a startup founded originally in Manchester, England.
S most advanced features are now available to free users. You And, the restrictive and inconsistent licensing of so-called ‘open’ AI models is creating significant uncertainty, particularly for commercial adoption, Nick Vidal, head of community at the Open Source Initiative, told TechCrunch. While these models are marketed as open, the actual terms impose various legal and practical hurdles that deter businesses from integrating them into their products or services.
S Kate Rooney sits down with Garry Tan, Y Combination president and CEO, at the accelerator On Inside the Code, Ankit Kumar, Sesame, and Anjney Midha, a16z on the Future of Voice AI. What goes into building a truly natural-sounding AI voice? Sesame’s cofounder and CTO, Ankit Kumar, joins a16z’s Anjney Midha for a deep dive into the research and engineering behind their voice technology.
Then, Nate B. Jones explains how AI is making intelligence cheaper, but software strategies built on user lock-in are failing. Historically, SaaS companies relied on retaining users by making it difficult to switch. However, as AI lowers the cost of building and refactoring, users move between tools more freely. The real challenge now is data interoperability—data remains siloed, making AI-generated content and workflows hard to integrate.
We close out with, AI is getting expensive…but it doesn’t have to be. NetworkChuck found a way to access all the major AI models– ChatGPT, Claude, Gemini, even Grok – without paying for multiple expensive subscriptions. Not only does he get unlimited access to the newest models, but he also has better security, more privacy, and a ton of features… this might be the best way to use AI.
Thats all for today, but AI is moving fast — subscribe and follow for more Neural News.
Scientists have unlocked a way to read magnetic orientation at record-breaking speeds using terahertz.
Terahertz radiation refers to the electromagnetic waves that occupy the frequency range between microwaves and infrared light, typically from about 0.1 to 10 terahertz (THz). This region of the electromagnetic spectrum is notable for its potential applications across a wide variety of fields, including imaging, telecommunications, and spectroscopy. Terahertz waves can penetrate non-conducting materials such as clothing, paper, and wood, making them particularly useful for security screening and non-destructive testing. In spectroscopy, they can be used to study the molecular composition of substances, as many molecules exhibit unique absorption signatures in the terahertz range.

Microsoft has reinstated the ‘Material Theme – Free’ and ‘Material Theme Icons – Free’ extensions on the Visual Studio Marketplace after finding that the obfuscated code they contained wasn’t actually malicious.
The two VSCode extensions, which count over 9 million installs, were pulled from the VSCode Marketplace in late February over security risks, and their publisher, Mattia Astorino (aka ‘equinusocio’) was banned from the platform.
“A member of the community did a deep security analysis of the extension and found multiple red flags that indicate malicious intent and reported this to us,” stated a Microsoft employee at the time.

A hospital that wants to use a cloud computing service to perform artificial intelligence data analysis on sensitive patient records needs a guarantee those data will remain private during computation. Homomorphic encryption is a special type of security scheme that can provide this assurance.
The technique encrypts data in a way that anyone can perform computations without decrypting the data, preventing others from learning anything about underlying patient records. However, there are only a few ways to achieve homomorphic encryption, and they are so computationally intensive that it is often infeasible to deploy them in the real world.
MIT researchers have developed a new theoretical approach to building homomorphic encryption schemes that is simple and relies on computationally lightweight cryptographic tools. Their technique combines two tools so they become more powerful than either would be on its own. The researchers leverage this to construct a “somewhat homomorphic” encryption scheme—that is, it enables users to perform a limited number of operations on encrypted data without decrypting it, as opposed to fully homomorphic encryption that can allow more complex computations.



Rodolfo Llinas tells the story of how he has developed bundles of nanowires thinner than spider webs that can be inserted into the blood vessels of human brains.
While these wires have so far only been tested in animals, they prove that direct communication with the deep recesses of the brain may not be so far off. To understand just how big of a breakthrough this is—US agents from the National Security Agency quickly showed up at the MIT laboratory when the wires were being developed.
What does this mean for the future? It might be possible to stimulate the senses directly — creating visual perceptions, auditory perceptions, movements, and feelings. Deep brain stimulation could create the ultimate virtual reality. Not to mention, direct communication between man and machine or human brain to human brain could become a real possibility.
Llinas poses compelling questions about the potentials and ethics of his technology.