Hacker group discloses the ability to encrypt an RTU device using ransomware, leading to reactions from Claroty and SynSaber.


The Guardian dice que un incidente cibernético a fines de diciembre de 2022 que provocó que el periódico británico cerrara sus oficinas durante semanas fue causado por ransomware e informó al personal el miércoles que los hackers habían accedido a sus datos.
Un correo electrónico enviado a su personal por la directora ejecutiva de Guardian Media Group Anna Bateson y la editora en jefe Katharine Viner dijeron que el ataque probablemente fue provocado por un correo electrónico de phishing.
El diario no entregó detalles de los datos expuestos aunque aclaró que no se ha visto afectado ningún dato personal de sus lectores o del personal en sus oficinas de EE.UU. o Australia.
Researchers from the cyber security firm Imperva Red Team have disclosed information on a newly found and fixed vulnerability that affected over 2.5 billion Google Chrome users as well as all Chromium-based browsers such as Edge and Opera.
The vulnerability, which is identified as CVE-2022–3656, makes it possible for remote attackers to acquire sensitive user data such as passwords for cloud service providers and knowledge about cryptocurrency wallets. After further investigation, it was determined that the problem was caused by the manner in which the Chrome browser dealt with symlinks when processing directories and files.
Because of this vulnerability, an attacker can use social engineering to convince a victim to visit a website that has been compromised and then download a ZIP archive file from that website. The file will contain a symlink to a valuable folder or file that is already present on the device, such as wallet keys. The user is requested to input their recovery keys whenever this file is sent back to this site as a component of an infection chain, such as a crypto wallet service.
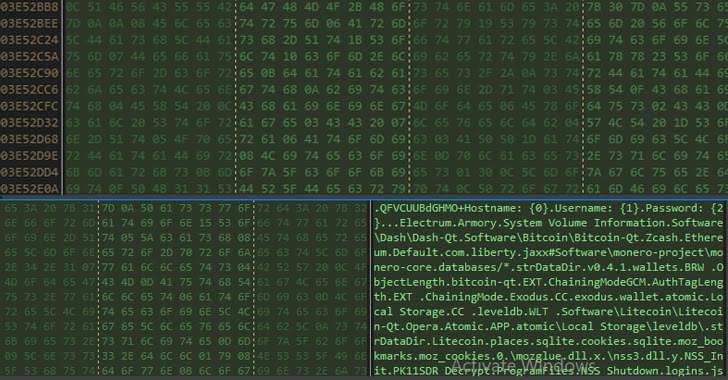
A new malware campaign has been observed targeting Italy with phishing emails designed to deploy an information stealer on compromised Windows systems.
“The info-stealer malware steals sensitive information like system info, crypto wallet and browser histories, cookies, and credentials of crypto wallets from victim machines,” Uptycs security researcher Karthickkumar Kathiresan said in a report.
Details of the campaign were first disclosed by Milan-based IT services firm SI.net last month.

This post is also available in:  עברית (Hebrew)
עברית (Hebrew)
Hackers constantly improve at penetrating cyber defenses to steal valuable documents. So some researchers propose using an artificial-intelligence algorithm to hopelessly confuse them, once they break-in, by hiding the real deal amid a mountain of convincing fakes. The algorithm, called Word Embedding–based Fake Online Repository Generation Engine (WE-FORGE), generates decoys of patents under development. But someday it could “create a lot of fake versions of every document that a company feels it needs to guard,” says its developer, Dartmouth College cybersecurity researcher V. S. Subrahmanian.
If hackers were after, say, the formula for a new drug, they would have to find the relevant needle in a haystack of fakes. This could mean checking each formula in detail—and perhaps investing in a few dead-end recipes. “The name of the game here is, ‘Make it harder,’” Subrahmanian explains. “‘Inflict pain on those stealing from you.’”



In this article, let us see how to build a potential darkweb monitoring tool out of ChatGPT
The dark web is a notorious and often misunderstood part of the internet, known for its anonymous communication and the buying and selling of illegal goods and services. It is not indexed by traditional search engines and is only accessible through specialized software, such as the Tor browser.
While the dark web can be a breeding ground for criminal activity, it is also a valuable resource for cyber security firms, law enforcement agencies and cybersecurity and threat intelligence individuals looking to track and monitor illegal activities.
What would happen if you combined the power of artificial intelligence with a human’s intellect and creativity? That’s the question Hack My Dogma sought to answer with the groundbreaking new series of videos featuring conversations between an AI GPT-3 created by OpenAI and Marcus, a human.
Through these videos, viewers can experience the power of AI first hand and get a glimpse into the potential of artificial intelligence, as well as what the future may hold.
In the series, Marcus and the AI discuss a range of topics such as IT, graphics engines, artificial intelligence, the singularity, and more.
Even more impressive is the computer animated model of GPT-3, which was created to represent GPT-3’s self-image. This model was rendered using synthesia.io, giving viewers a unique glimpse into the mind of the #AI. Join the conversation today to experience the power of AI for yourself and explore the potential of artificial intelligence!
Openai.com.
synthesia.io.
@YannicKilcher I would like, to do the same with GPT-4Chan.
A Russian hacking team known as Cold River targeted three nuclear research laboratories in the United States this past summer, according to internet records reviewed by Reuters and five cyber security experts.
#unitedstates #russia #wion.
About Channel:
WION The World is One News, examines global issues with in-depth analysis. We provide much more than the news of the day. Our aim to empower people to explore their world. With our Global headquarters in New Delhi, we bring you news on the hour, by the hour. We deliver information that is not biased. We are journalists who are neutral to the core and non-partisan when it comes to the politics of the world. People are tired of biased reportage and we stand for a globalised united world. So for us the World is truly One.
Please keep discussions on this channel clean and respectful and refrain from using racist or sexist slurs as well as personal insults.
Check out our website: http://www.wionews.com.
Connect with us on our social media handles:
Facebook: https://www.facebook.com/WIONews.
Twitter: https://twitter.com/WIONews.
Follow us on Google News for latest updates.