TamperedChef spreads through fake installers and SEO abuse, delivering a persistent JavaScript backdoor across multiple sectors.


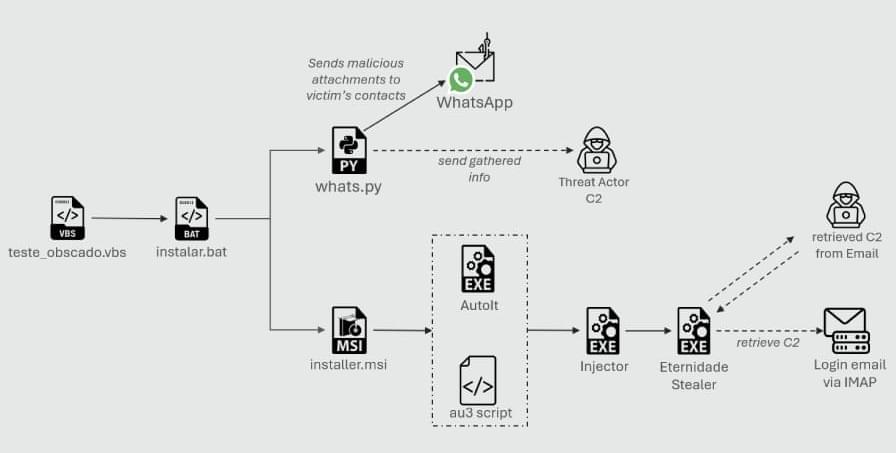
Cybersecurity researchers have disclosed details of a new campaign that leverages a combination of social engineering and WhatsApp hijacking to distribute a Delphi-based banking trojan named Eternidade Stealer as part of attacks targeting users in Brazil.
“It uses Internet Message Access Protocol (IMAP) to dynamically retrieve command-and-control (C2) addresses, allowing the threat actor to update its C2 server,” Trustwave SpiderLabs researchers Nathaniel Morales, John Basmayor, and Nikita Kazymirskyi said in a technical breakdown of the campaign shared with The Hacker News.
It is distributed through a WhatsApp worm campaign, with the actor now deploying a Python script, a shift from previous PowerShell-based scripts to hijack WhatsApp and spread malicious attachments.

Cybersecurity researchers have discovered a set of seven npm packages published by a single threat actor that leverages a cloaking service called Adspect to differentiate between real victims and security researchers to ultimately redirect them to sketchy crypto-themed sites.
The malicious npm packages, published by a threat actor named “dino_reborn” between September and November 2025, are listed below. The npm account no longer exists on npm as of writing.


A global campaign dubbed ShadowRay 2.0 hijacks exposed Ray Clusters by exploiting an old code execution flaw to turn them into a self-propagating cryptomining botnet.
Developed by Anyscale, the Ray open-source framework allows building and scaling AI and Python applications in a distributed computing ecosystem organized in clusters, or head nodes.
According to researchers at runtime security company Oligo, a threat actor they track as IronErn440 is using AI-generated payloads to compromise vulnerable Ray infrastructure that is reachable over the public internet.
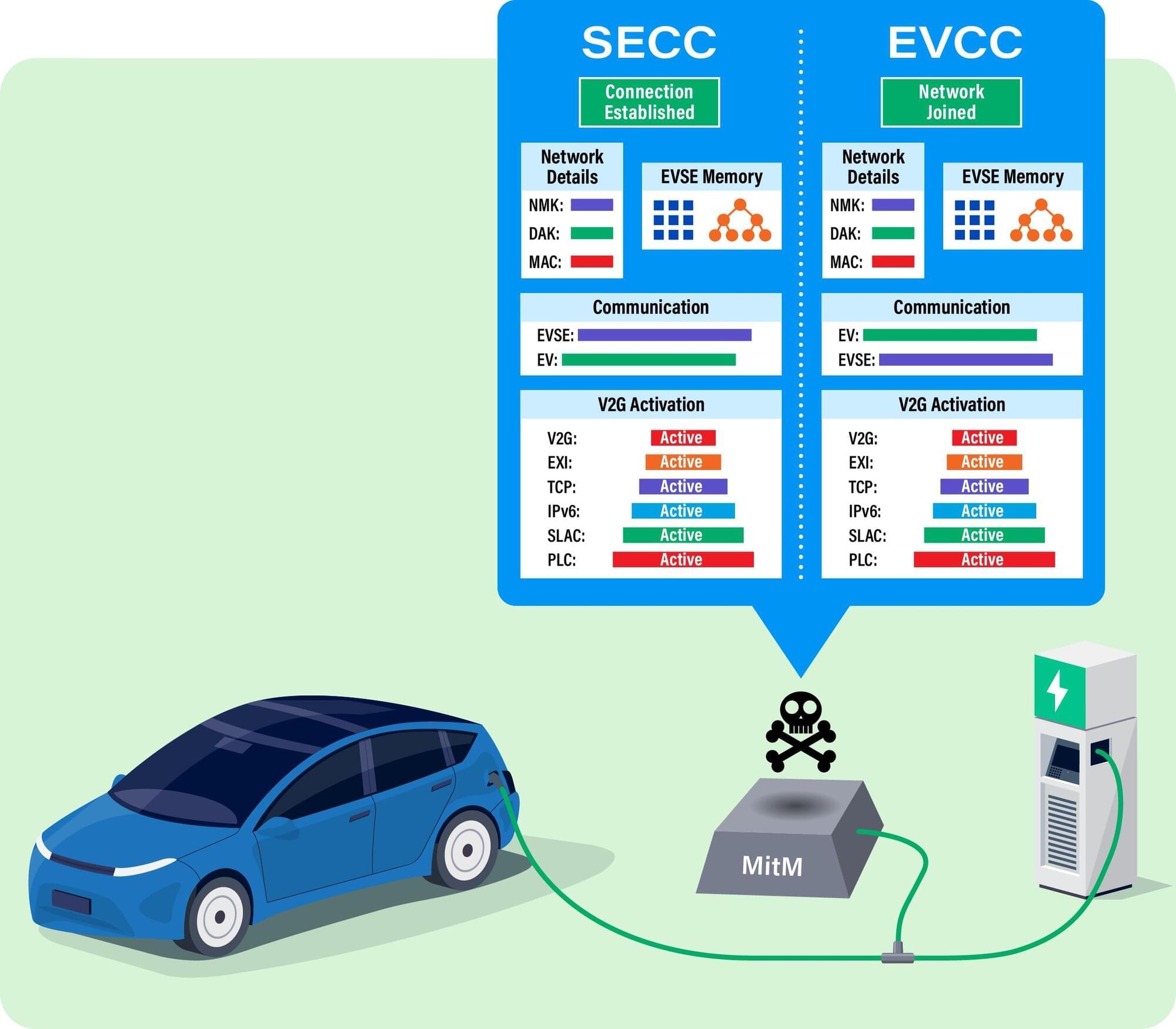
Southwest Research Institute identified a security vulnerability in a standard protocol governing communications between electric vehicles (EV) and EV charging equipment. The research prompted the Cybersecurity & Infrastructure Security Agency (CISA) to issue a security advisory related to the ISO 15118 vehicle-to-grid communications standard.


The decades-old “finger” command is making a comeback„ with threat actors using the protocol to retrieve remote commands to execute on Windows devices.
In the past, people used the finger command to look up information about local and remote users on Unix and Linux systems via the Finger protocol, a command later added to Windows. While still supported, it’s rarely used today compared to its popularity decades ago.
When executed, the finger command returns basic information about a user, including their login name, name (if set in /etc/passwd), home directory, phone numbers, last seen, and other details.