RapperBot launched 370,000 DDoS attacks on 18,000 victims in 80+ countries since 2021, DOJ seizes botnet.




A software vulnerability checker with the potential to become a repair shop could keep critical computer systems one step ahead.
High-profile cyberattacks, such as the one that compromised British retailer Marks & Spencer’s customer data in April 2025, highlight the need for better ways to detect software vulnerabilities in the computer systems that increasingly control everything, from oil pipelines to hospital records.
To help, an international research team including Khalifa University’s Merouane Debbah, has developed SecureQwen, a smart software checker that automatically detects and flags vulnerabilities for repair. Powered by an AI model trained in the language of computer code, SecureQwen could even identify weaknesses that it had not explicitly been taught or come upon before.
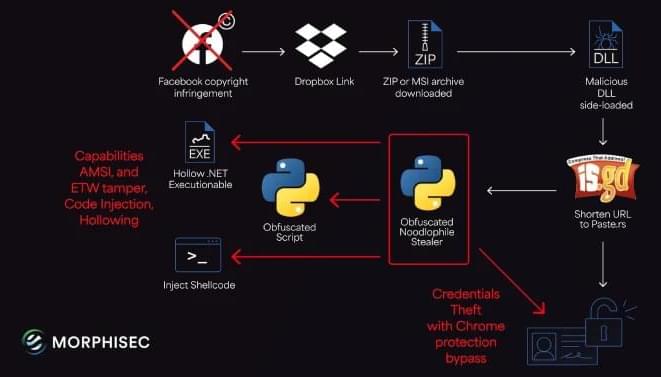
But the latest iteration of the Noodlophile attacks exhibits notable deviation, particularly when it comes to the use of legitimate software vulnerabilities, obfuscated staging via Telegram, and dynamic payload execution.
It all starts with a phishing email that seeks to trick employees into downloading and running malicious payloads by inducing a false sense of urgency, claiming copyright violations on specific Facebook Pages. The messages originate from Gmail accounts in an effort to evade suspicion.
Present within the message is a Dropbox link that drops a ZIP or MSI installer, which, in turn, sideloads a malicious DLL using legitimate binaries associated with Haihaisoft PDF Reader to ultimately launch the obfuscated Noodlophile stealer, but not before running batch scripts to establish persistence using Windows Registry.



A state-sponsored espionage campaign is targeting foreign embassies in South Korea to deploy XenoRAT malware from malicious GitHub repositories.
According to Trellix researchers, the campaign has been running since March and is ongoing, having launched at least 19 spearphishing attacks against high-value targets.
Although infrastructure and techniques match the pllaybook of North Korean actor Kimsuky (APT43), there are signs that better match China-based operatives, the researchers say.

The source code for version 3 of the ERMAC Android banking trojan has been leaked online, exposing the internals of the malware-as-a-service platform and the operator’s infrastructure.
The code base was discovered in an open directory by Hunt.io researchers while scanning for exposed resources in March 2024.
They located an archive named Ermac 3.0.zip, which contained the malware’s code, including backend, frontend (panel), exfiltration server, deployment configurations, and the trojan’s builder and obfuscator.

