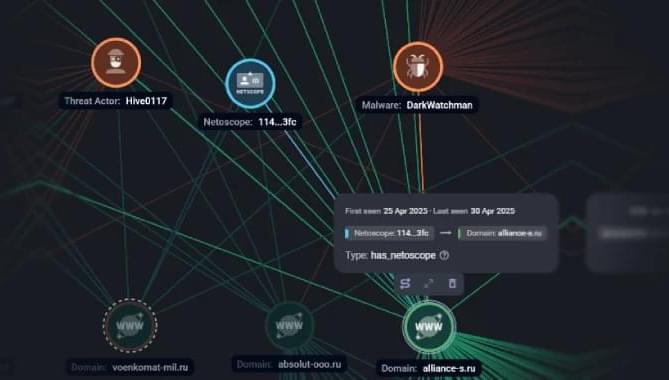
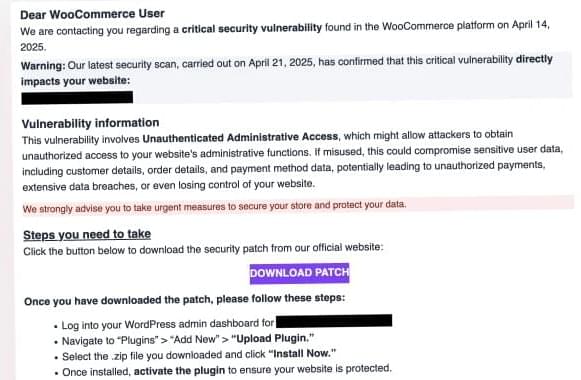
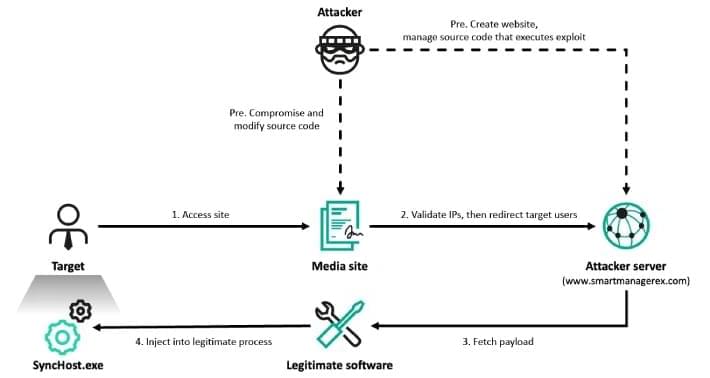
Phishing attacks deliver DarkWatchman and Sheriff malware; targets span Russia, Ukraine, Baltics, with stealth and persistence tactics.



Employee benefits administration firm VeriSource Services is warning that a data breach exposed the personal information of four million people.
VeriSource is a Texas-based employee benefits administration and HR outsourcing solutions provider with diverse clients across the U.S.
The firm has begun data breach notifications to impacted individuals about a cybersecurity incident that occurred in February 2024, but the impact of which it took them until April 2025 to evaluate.

Internet services giant Cloudflare says it mitigated a record number of DDoS attacks in 2024, recording a massive 358% year-over-year jump and a 198% quarter-over-quarter increase.
These figures come from Cloudflare’s 2025 Q1 DDoS Report, where the company says it mitigated a total of 21.3 million DDoS attacks in 2024.
However, 2025 is looking to be an even bigger problem for online entities and companies, with Cloudflare already responding to 20.5 million DDoS attacks in just the first quarter of 2025.
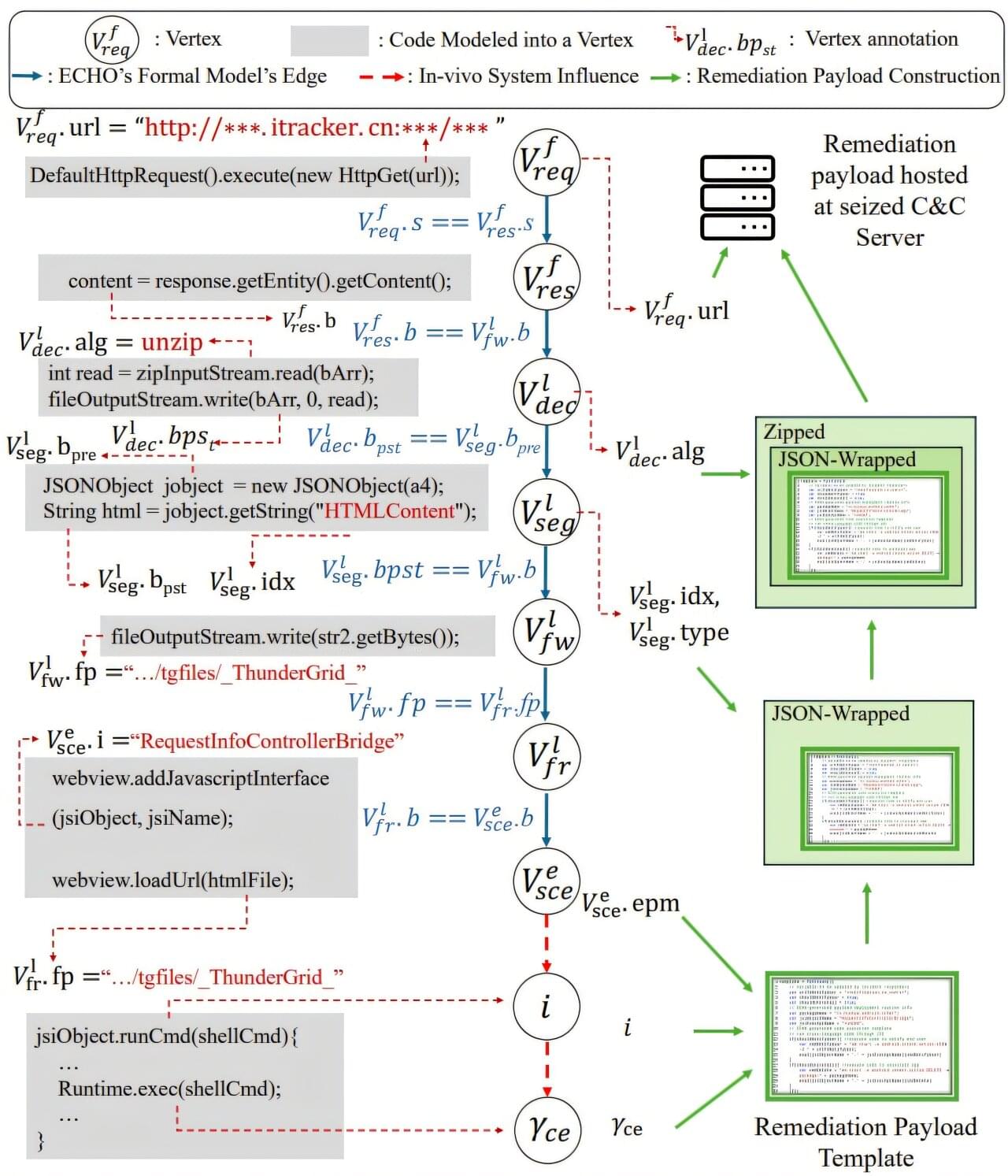
Cyberattacks can snare workflows, put vulnerable client information at risk, and cost corporations and governments millions of dollars. A botnet—a network infected by malware—can be particularly catastrophic. A new Georgia Tech tool automates the malware removal process, saving engineers hours of work and companies money.
The tool, ECHO, turns malware against itself by exploiting its built-in update mechanisms and preventing botnets from rebuilding. ECHO is 75% effective at removing botnets. Removing malware used to take days or weeks to fix, but can now be resolved in a few minutes. Once a security team realizes their system is compromised, they can now deploy ECHO, which works fast enough to prevent the botnet from taking down an entire network.
“Understanding the behavior of the malware is usually very hard with little reward for the engineer, so we’ve made an automatic solution,” said Runze Zhang, a Ph.D. student in the School of Cybersecurity and Privacy (SCP) and the School of Electrical and Computer Engineering.

Darcula adds GenAI tools + Lowers phishing skills barrier + 25,000 scam pages taken down.